Internet Control Message Protocol (ICMP) Parameters
Type 0 — Echo Reply
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 1 — Unassigned
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 2 — Unassigned
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. |
||
Type 3 — Destination Unreachable
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Net Unreachable | [RFC792] |
| 1 | Host Unreachable | [RFC792] |
| 2 | Protocol Unreachable | [RFC792] |
| 3 | Port Unreachable | [RFC792] |
| 4 | Fragmentation Needed and Don’t Fragment was Set |
[RFC792] |
| 5 | Source Route Failed | [RFC792] |
| 6 | Destination Network Unknown | [RFC1122] |
| 7 | Destination Host Unknown | [RFC1122] |
| 8 | Source Host Isolated | [RFC1122] |
| 9 | Communication with Destination Network is Administratively Prohibited |
[RFC1122] |
| 10 | Communication with Destination Host is Administratively Prohibited |
[RFC1122] |
| 11 | Destination Network Unreachable for Type of Service |
[RFC1122] |
| 12 | Destination Host Unreachable for Type of Service |
[RFC1122] |
| 13 | Communication Administratively Prohibited | [RFC1812] |
| 14 | Host Precedence Violation | [RFC1812] |
| 15 | Precedence cutoff in effect | [RFC1812] |
Type 4 — Source Quench (Deprecated)
- Reference
- [RFC792][RFC6633]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 5 — Redirect
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Redirect Datagram for the Network (or subnet) | |
| 1 | Redirect Datagram for the Host | |
| 2 | Redirect Datagram for the Type of Service and Network | |
| 3 | Redirect Datagram for the Type of Service and Host |
Type 6 — Alternate Host Address (Deprecated)
- Reference
- [JBP][RFC6918]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Alternate Address for Host |
Type 7 — Unassigned
| Codes | Description | Reference |
|---|---|---|
No registrations at this time. |
||
Type 8 — Echo
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 9 — Router Advertisement
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC1256][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Normal router advertisement | [RFC3344] |
| 16 | Does not route common traffic | [RFC3344] |
Type 10 — Router Selection
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC1256][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 11 — Time Exceeded
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Time to Live exceeded in Transit | |
| 1 | Fragment Reassembly Time Exceeded |
Type 12 — Parameter Problem
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Pointer indicates the error | |
| 1 | Missing a Required Option | [RFC1108] |
| 2 | Bad Length |
Type 13 — Timestamp
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 14 — Timestamp Reply
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC792][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 15 — Information Request (Deprecated)
- Reference
- [RFC792][RFC6918]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 16 — Information Reply (Deprecated)
- Reference
- [RFC792][RFC6918]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 17 — Address Mask Request (Deprecated)
- Reference
- [RFC950][RFC6918]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 18 — Address Mask Reply (Deprecated)
- Reference
- [RFC950][RFC6918]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Code |
Type 19 — Reserved (for Security)
- Reference
- [Solo]
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.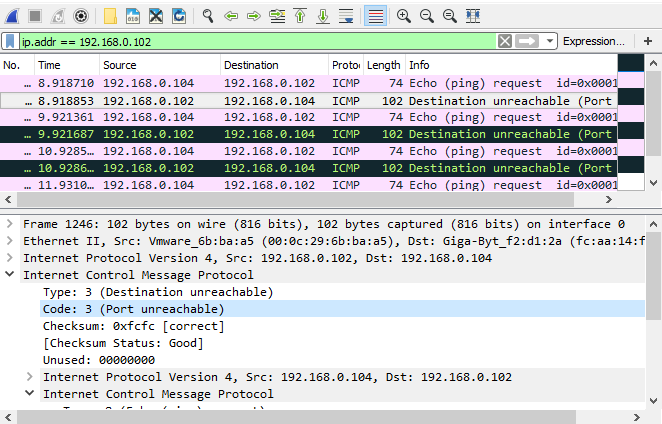 |
||
Types 20-29 — Reserved (for Robustness Experiment)
- Reference
- [ZSu]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 30 — Traceroute (Deprecated)
- Reference
- [RFC1393][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 31 — Datagram Conversion Error (Deprecated)
- Reference
- [RFC1475][RFC6918]
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.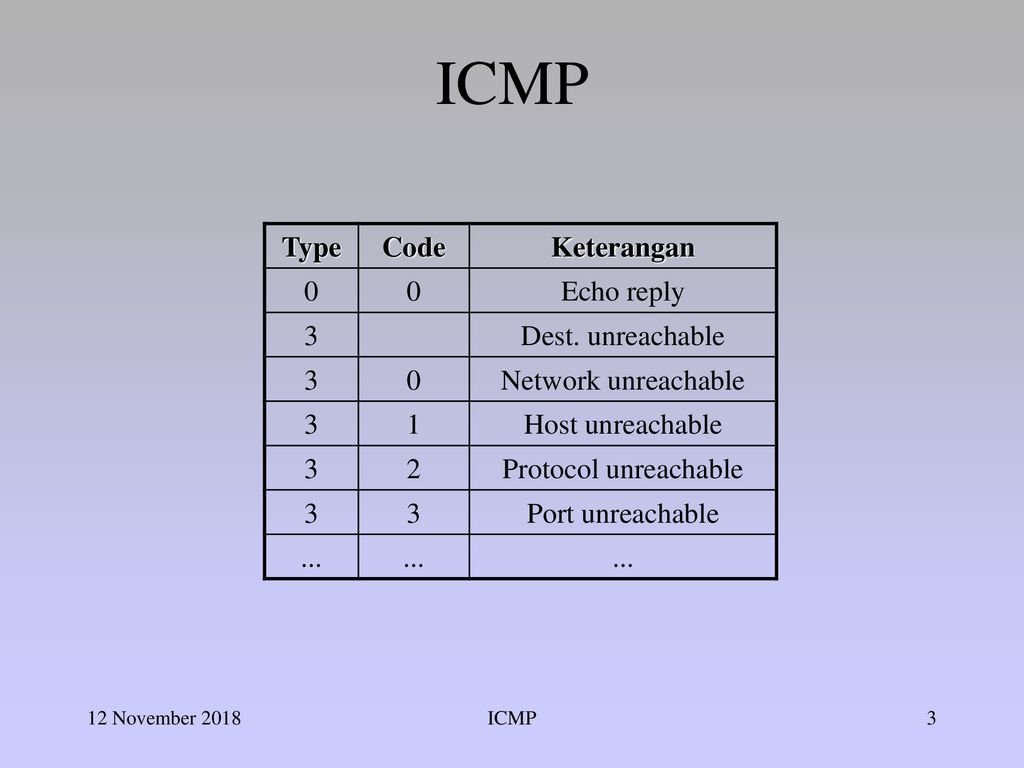 |
||
Type 32 — Mobile Host Redirect (Deprecated)
- Reference
- [David_Johnson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 33 — IPv6 Where-Are-You (Deprecated)
- Reference
- [Simpson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 34 — IPv6 I-Am-Here (Deprecated)
- Reference
- [Simpson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.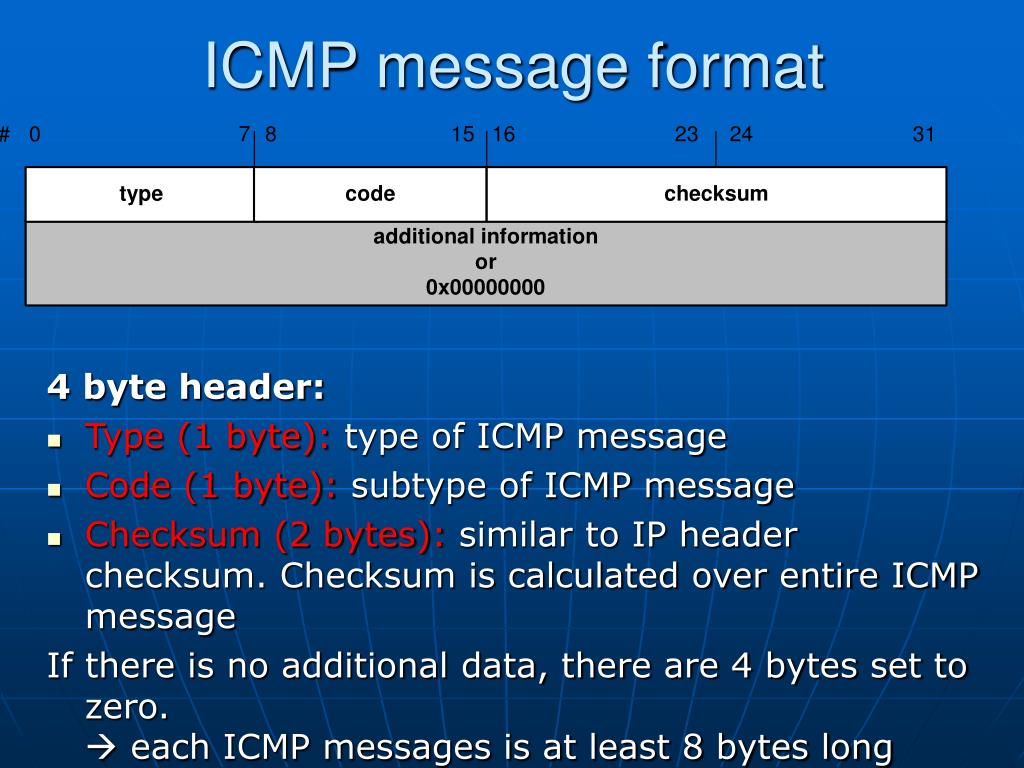 |
||
Type 35 — Mobile Registration Request (Deprecated)
- Reference
- [Simpson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 36 — Mobile Registration Reply (Deprecated)
- Reference
- [Simpson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 37 — Domain Name Request (Deprecated)
- Reference
- [RFC1788][RFC6918]
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.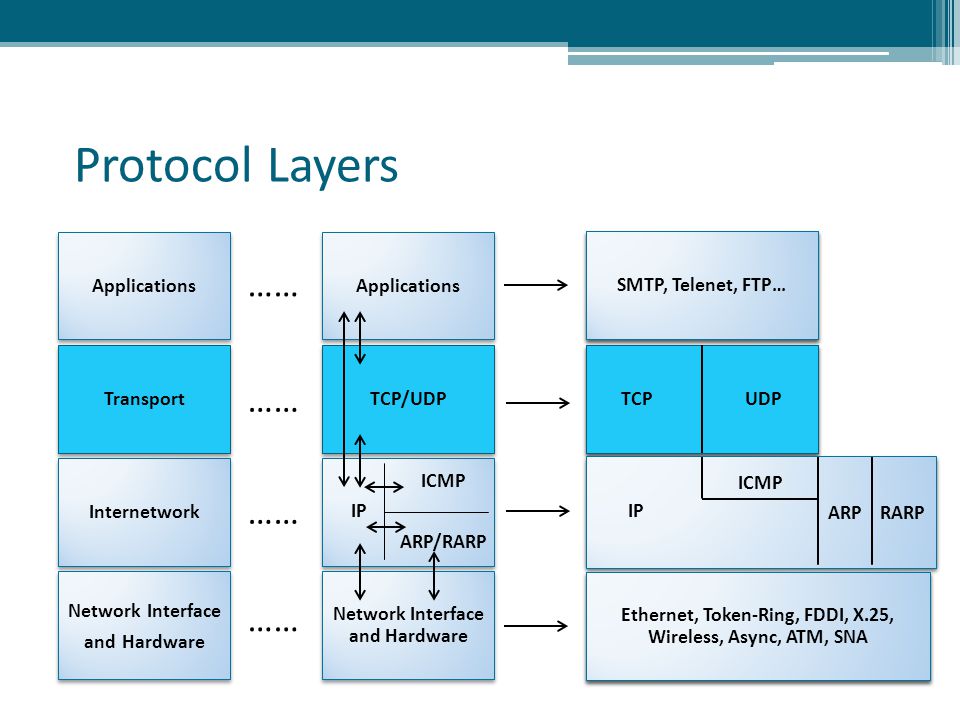 |
||
Type 38 — Domain Name Reply (Deprecated)
- Reference
- [RFC1788][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 39 — SKIP (Deprecated)
- Reference
- [Markson][RFC6918]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 40 — Photuris
- Registration Procedure(s)
-
IESG Approval or Standards Action
- Reference
- [RFC2521][RFC2780]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Bad SPI | |
| 1 | Authentication Failed | |
| 2 | Decompression Failed | |
| 3 | Decryption Failed | |
| 4 | Need Authentication | |
| 5 | Need Authorization |
Type 41 — ICMP messages utilized by experimental mobility protocols such as Seamoby
- Registration Procedure(s)
-
Specification Required or IESG Approval
- Expert(s)
-
Unassigned
- Reference
- [RFC4065]
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.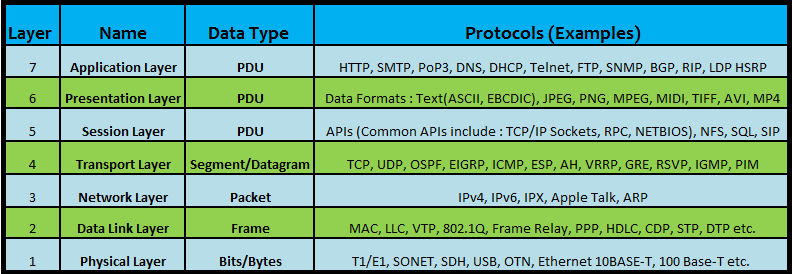 |
||
Type 42 — Extended Echo Request
- Registration Procedure(s)
-
First Come First Served
- Reference
- [RFC8335]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Error | [RFC8335] |
| 1-255 | Unassigned |
Type 43 — Extended Echo Reply
- Registration Procedure(s)
-
First Come First Served
- Reference
- [RFC8335]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | No Error | [RFC8335] |
| 1 | Malformed Query | [RFC8335] |
| 2 | No Such Interface | [RFC8335] |
| 3 | No Such Table Entry | [RFC8335] |
| 4 | Multiple Interfaces Satisfy Query | [RFC8335] |
| 5-255 | Unassigned |
Types 44-252 — Unassigned
| Codes | Description | Reference |
|---|---|---|
No registrations at this time.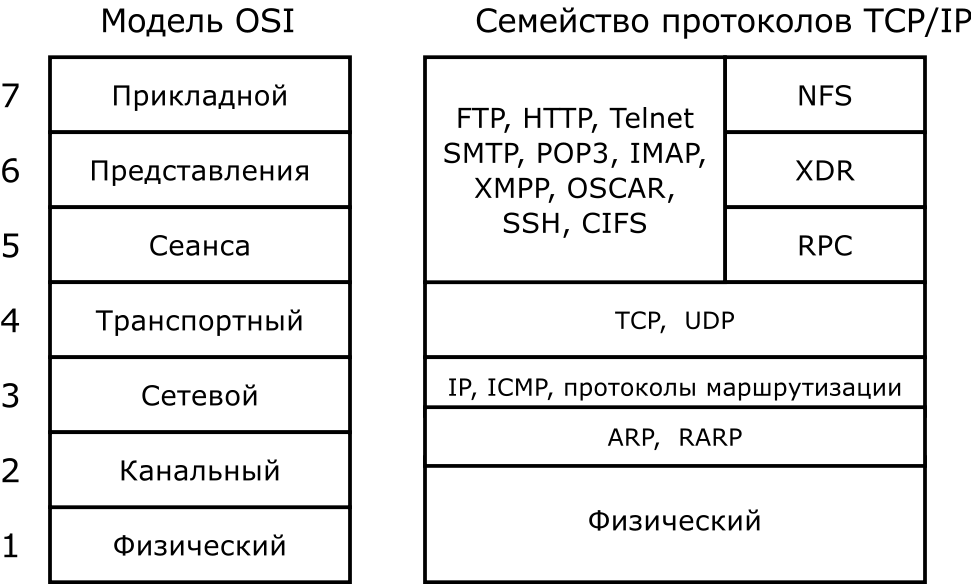 |
||
Type 253 — RFC3692-style Experiment 1 [1]
- Registration Procedure(s)
-
Standards Action or IESG Approval
- Reference
- [RFC4727]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Type 254 — RFC3692-style Experiment 2 [1]
- Registration Procedure(s)
-
Standards Action or IESG Approval
- Reference
- [RFC4727]
| Codes | Description | Reference |
|---|---|---|
| No registrations at this time. | ||
Sub-types — Class 1 — MPLS Label Stack Class
- Registration Procedure(s)
-
First Come First Served
- Reference
- [RFC4950]
- Available Formats
-
CSV
| C-Type (Value) | Description | Reference |
|---|---|---|
| 0 | Reserved | [RFC4950] |
| 1 | Incoming MPLS Label Stack | [RFC4950] |
| 2-246 | Unassigned | |
| 247-255 | Reserved for private use | [RFC4950] |
Sub-types — Class 2 — Interface Information Object
- Reference
- [RFC5837]
- Available Formats
-
CSV
| C-Type (Value) | Description | Reference |
|---|---|---|
| 0-1 | Interface Role field | [RFC5837] |
| 2 | Unallocated — allocatable with Standards Action | [RFC5837] |
| 3 | Unallocated — allocatable with Standards Action | [RFC5837] |
| 4 | ifIndex included | [RFC5837] |
| 5 | IP Address Sub-object included | [RFC5837] |
| 6 | Name Sub-object included | [RFC5837] |
| 7 | MTU included | [RFC5837] |
Sub-types — Class 2 — Interface Information Object — Interface Roles
- Available Formats
-
CSV
| Value | Description | Reference |
|---|---|---|
| 0 | Incoming IP Interface | [RFC5837] |
| 1 | Sub-IP Component of Incoming IP Interface | [RFC5837] |
| 2 | Outgoing IP Interface | [RFC5837] |
| 3 | IP Next-hop | [RFC5837] |
Sub-types — Class 3 — Interface Identification Object
- Registration Procedure(s)
-
First Come First Served
- Reference
- [RFC8335]
- Available Formats
-
CSV
| Codes | Description | Reference |
|---|---|---|
| 0 | Reserved | [RFC8335] |
| 1 | Identifies Interface By Name | [RFC8335] |
| 2 | Identifies Interface By Index | [RFC8335] |
| 3 | Identifies Interface By Address | [RFC8335] |
| 4-255 | Unassigned |
Sub-types — Class 4 — Extended Information
- Registration Procedure(s)
-
Standards Action
- Reference
- [RFC8883]
- Available Formats
-
CSV
| Value | Description | Reference |
|---|---|---|
| 0 | Reserved | [RFC8883] |
| 1 | Pointer | [RFC8883] |
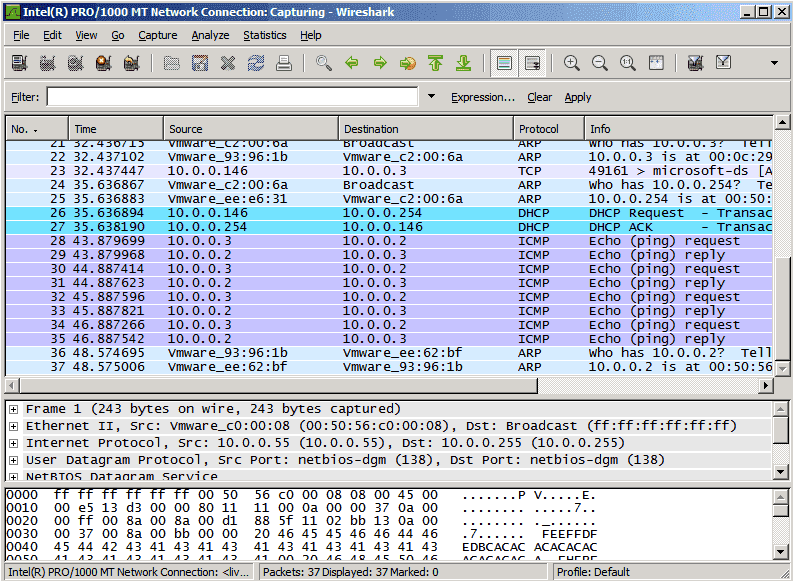
ICMP — Destination Unreachable Message Analysis
The ‘ICMP Destination unreachable‘ message is quite interesting, because it doesn’t actually contain one message, but infact six! This means that the ICMP Destination unreachable futher breaks down into 6 different messages.
This article will analyse all six destination unreachable messages and explain which occasions each message is used. The table below shows an brief summary of the available messages and their code value contain in the ICMP header:
To make sure you don’t get confused, keep one thing in mind: The ICMP Destination unreachable is a generic ICMP message, the different code values or messages which are part of it are there to clarify the type of «Destination unreachable» message was received. It goes something like this: ICMP Destination unreachable.
The ICMP — Destination net unreachable message is one which a user would usually get from the gateway when it doesn’t know how to get to a particular network.
The ICMP — Destination host unreachable message is one which a user would usually get from the remote gateway when the destination host is unreachable.
If, in the destination host, the IP module cannot deliver the packet because the indicated protocol module or process port is not active, the destination host may send an ICMP destination protocol / port unreachable message to the source host.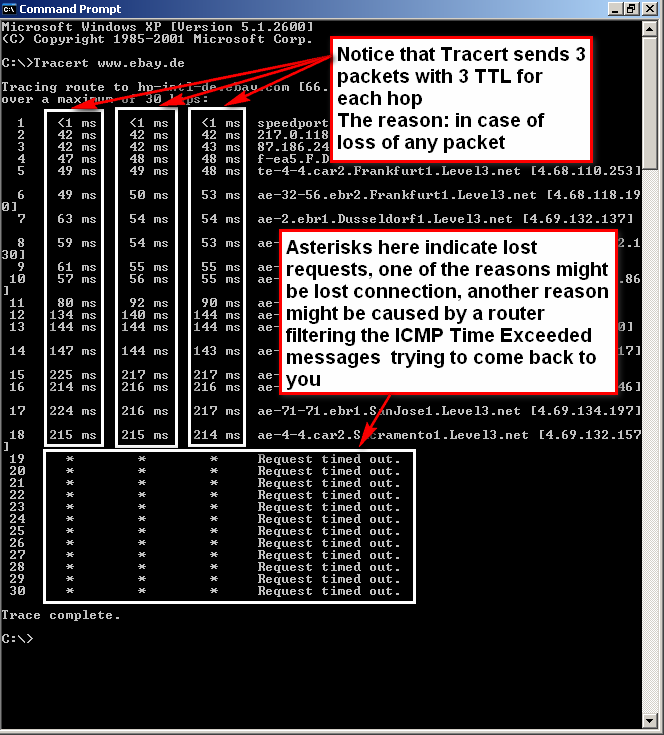
In another case, when a packet received must be fragmented to be forwarded by a gateway but the «Don’t Fragment» flag (DF) is on, the gateway must discard the packet and send an ICMP destination fragmentation needed and DF set unreachable message to the source host.
These ICMP messages are most useful when trying to troubleshoot a network. You can check to see if all routers and gateways are configured properly and have their routing tables updated and synchronised.
Let’s look at the packet structure of an ICMP destination unreachable packet:
Please read on as the following example will help you understand all the above.
The Analysis
When you open a DOS command prompt and type «ping 200.200.200.200», assuming that your workstation is NOT part of that network, then it would forward the ICMP Echo request to the gateway that’s configured in your TCP/IP properties.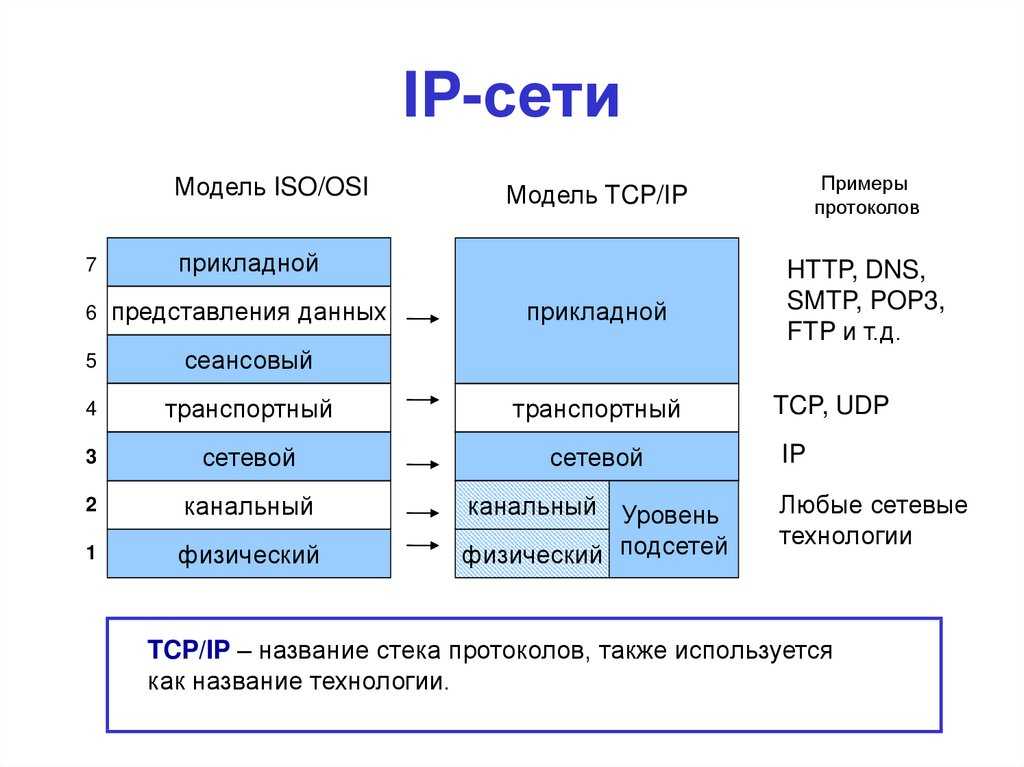 At that point, the gateway should be able to figure out where to forward the ICMP Echo request.
At that point, the gateway should be able to figure out where to forward the ICMP Echo request.
The gateway usually has a «default route» entry, this entry is used when the gateway doesn’t know where the network is. Now, if the gateway has no «default route» you would get an «ICMP Destination net unreachable» message when you try to get to a network which the gateway doesn’t know about. When you’re connected to the Internet via a modem, then your default gateway is the modem.
In order for me to demonstrate this, I set up my network in a way that should make it easy for you to see how everything works. I have provided a lot of pictures hoping to make it as easy as possible to understand.
I will analyse why and how you get an «ICMP — Destination net unreachable» message.
In the example above, I’ve setup my workstation to use the Linux server as a default gateway, which has an IP of 192.168.0.5.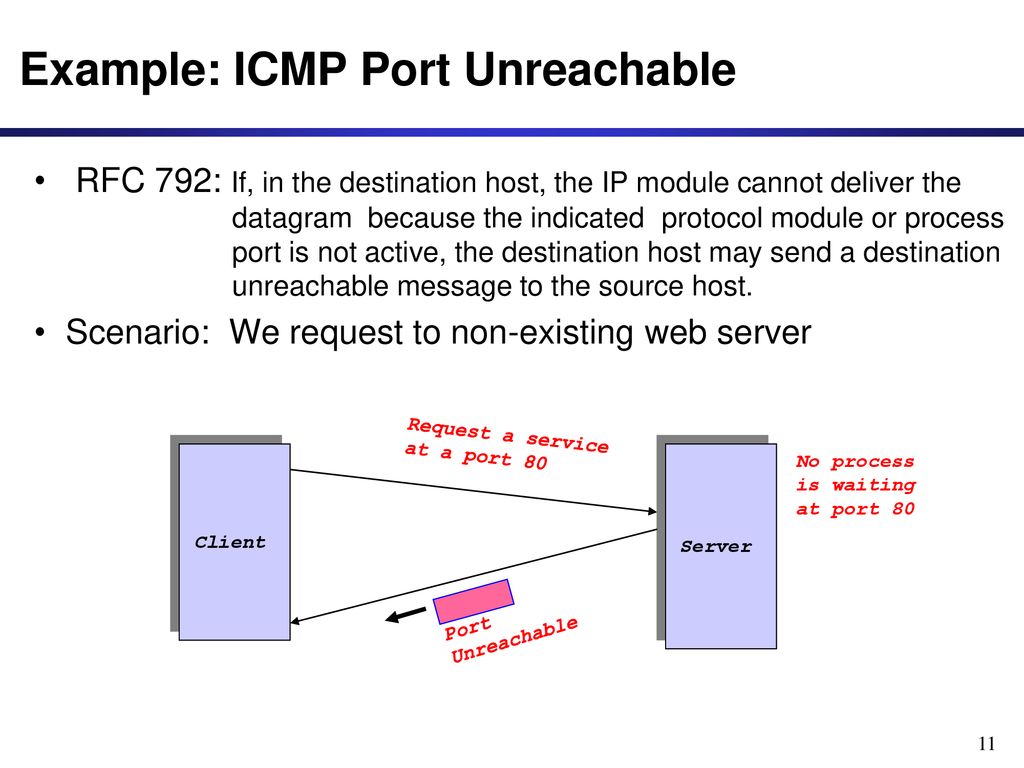 The Linux server also has a default gateway entry and this is IP: 192.168.0.1 (the Windows 2000 Server).
The Linux server also has a default gateway entry and this is IP: 192.168.0.1 (the Windows 2000 Server).
When my workstation attempts to ping (send an ICMP Echo request) to IP 200.200.200.200, it realises it’s on a different network, so it sends it to the Linux server, which in turn forwards it to its default gateway (the Win2k server) so it can then be forwarded to the Internet and eventually I should get a ping reply (ICMP Echo reply) if the host exists and has no firewall blocking ICMP echo requests.
Here is the packet which I captured and its analysis on the right:
When looking at the decoded packet you can see in the ICMP header section that the ICMP Type is equal to 8, so this confirms that it’s an ICMP Echo (ping). As mentioned earlier, we would expect to receive an ICMP echo reply.
Check out though what happens when the default gateway entry is removed from the Linux server:
Now what I did was to remove the default gateway entry from the Linux server. So when it gets a packet from my workstation, it wouldn’t know what to do with it. This is how you get the gateway to generate an «ICMP Destination net unreachable» message and send it back to the source host (my workstation).
So when it gets a packet from my workstation, it wouldn’t know what to do with it. This is how you get the gateway to generate an «ICMP Destination net unreachable» message and send it back to the source host (my workstation).
Here is a screen shot from the command prompt:
As you can see, the Linux server has returned an «ICMP Destination net unreachable». This is one of the six possible ‘ICMP Destination Unreachable’ messages as listed at the beginning of this page. The Linux server doesn’t know what to do with the packet since it has no way of getting to that 200.200.200.0 network, so it sends the «ICMP Destination net unreachable» message to my workstation, notifiying it that it doesnt know how to get to that network.
Let’s now take a look what the packet sniffer caught :
The decoded packet on the right shows that the Linux server (192.168.0.5) sent back to my workstation (192.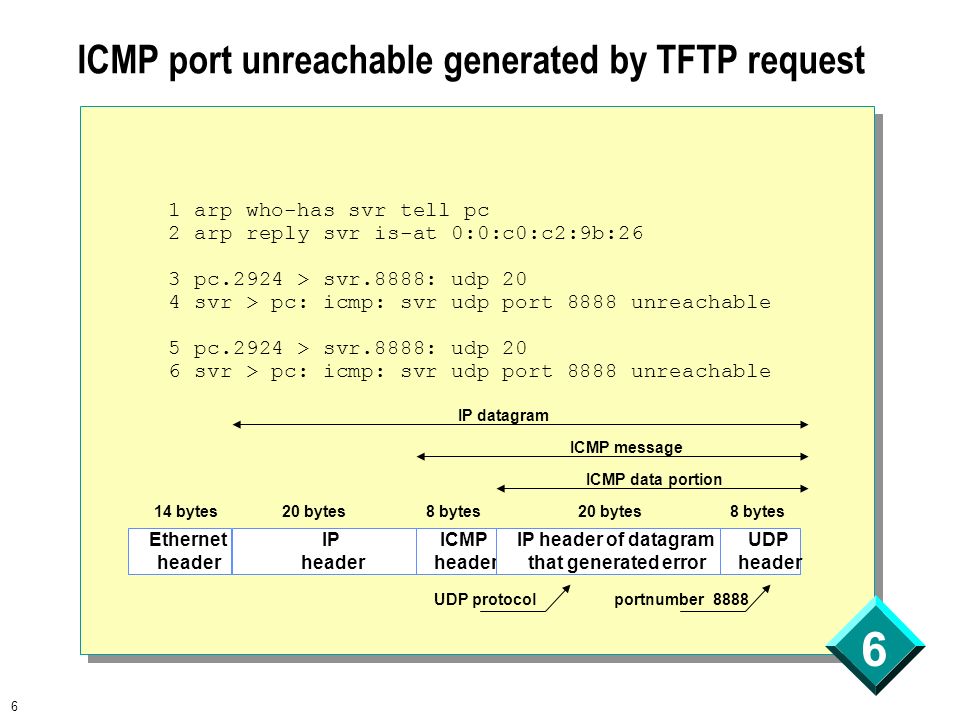 168.0.100) an ICMP Destination unreachable message (look at the ICMP type field, right under the ICMP header) but if you also check out the ICMP Code (highlighted field), it’s equal to 0, which means «net unreachable». Scrolling right at the top of this page, the first table clearly shows that when the code field has a value of 0, this is indeed a «net unreachable» message.
168.0.100) an ICMP Destination unreachable message (look at the ICMP type field, right under the ICMP header) but if you also check out the ICMP Code (highlighted field), it’s equal to 0, which means «net unreachable». Scrolling right at the top of this page, the first table clearly shows that when the code field has a value of 0, this is indeed a «net unreachable» message.
It is also worth noticing the «Returned IP header» which exists within the ICMP header. This is the IP header of the packet my workstation sent to the Linux server when it attempted to ping 200.200.200.200, and following that is 64 bits (8 bytes) of the original data.
This completed our discussion on the ICMP ‘Destination Unreachable’ generated packets.
Next — ICMP — Source Quench Message
ICMP port opener for the server / Sudo Null IT News
. After a little thought (the idea is not new), I decided to write a simple, so to speak, ICMP knocker, that is, opening ports by ping.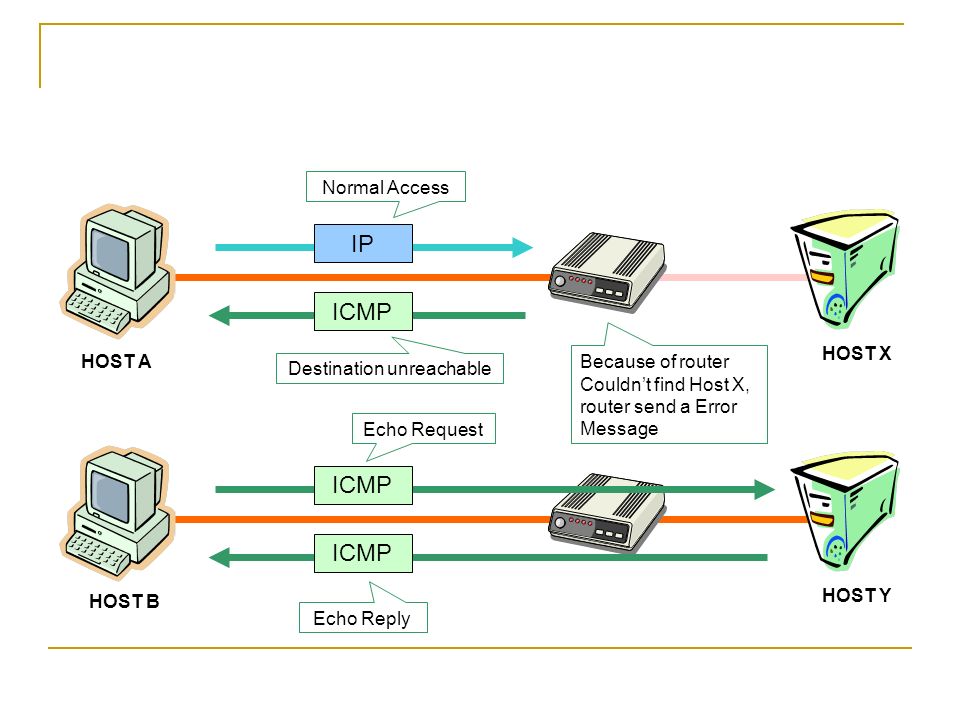 But ping is not simple, but with a certain message/packet size. Linux example:
But ping is not simple, but with a certain message/packet size. Linux example:
ping -s 999 -c1 mysrv.com
Where -s is the size of the message to be sent, -s is the number. If the message size matches, then the specified ports are opened for the sender’s IP address for a while and a message is sent about opening ports in Telegram. So to implement this craft you will need: ufw, curl, tcpdump:
apt install ufw curl tcpdump
and the script itself:
nano /opt/port-knocker.sh
#!/bin/bash
PING_SIZE=999
PORTS='tcp/22 tcp/443'
TIMEOUT=3600
TOKEN="121212XXXX:XXXXZZZZAAAAEEEERRRRQQQQGGGGTTTTHHHH"
CHATID="55555XXXX"
PACKAGE_SIZE=$(( $PING_SIZE + 28 ))
function allow_access {
RESULT=`ufw allow proto $PROTO from $SRC to $DST port $PORT`
echo "`date` _ PORT-knocker _ $SRC -> $DST:$PORT : $RESULT"
MESS="`uname -n` %0A`date` %0Aufw allow proto tcp from $SRC to $DST PORT $PORT %0A$RESULT"
curl -s "https://api.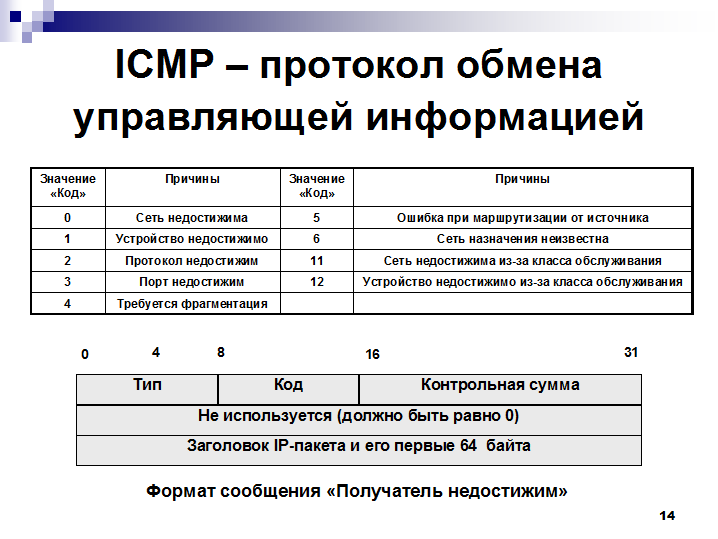 .*IP ||' | tr ':' ' ' | awk '{print $1" "$3 }'`
SRC=`echo $IP | awk {'print $1'}`
DST=`echo $IP | awk {'print $2'}`
if [ -n "$SRC" ] && [ -n "$DST" ]
then
for PPORT in ${PORTS}
do
PROTO=`echo $PPORT | sed 's|/| |g' | awk '{print $1}'`
PORT=`echo $PPORT | sed 's|/| |g' | awk '{print $2}'`
if ufw show added | grep "$DST" | grep "$SRC" | grep "$PORT"
then
deny_access
else
allow_access
deny_access
fi
done
fi
else
echo "`date` - Timeout, reload sniffer"
fi
done
.*IP ||' | tr ':' ' ' | awk '{print $1" "$3 }'`
SRC=`echo $IP | awk {'print $1'}`
DST=`echo $IP | awk {'print $2'}`
if [ -n "$SRC" ] && [ -n "$DST" ]
then
for PPORT in ${PORTS}
do
PROTO=`echo $PPORT | sed 's|/| |g' | awk '{print $1}'`
PORT=`echo $PPORT | sed 's|/| |g' | awk '{print $2}'`
if ufw show added | grep "$DST" | grep "$SRC" | grep "$PORT"
then
deny_access
else
allow_access
deny_access
fi
done
fi
else
echo "`date` - Timeout, reload sniffer"
fi
done
Where,
PING_SIZE — message size
PORTS=’tcp/22 tcp/443′ — protocol and port
TIMEOUT=3600 — port opening timeout in seconds
TOKEN — BotFather will tell the telegram on request «/mybots» -> «API Token»
CHATID — IDBot’s telegram will prompt «/getid»
Make the script executable:
chmod +x /opt/port-knocker. 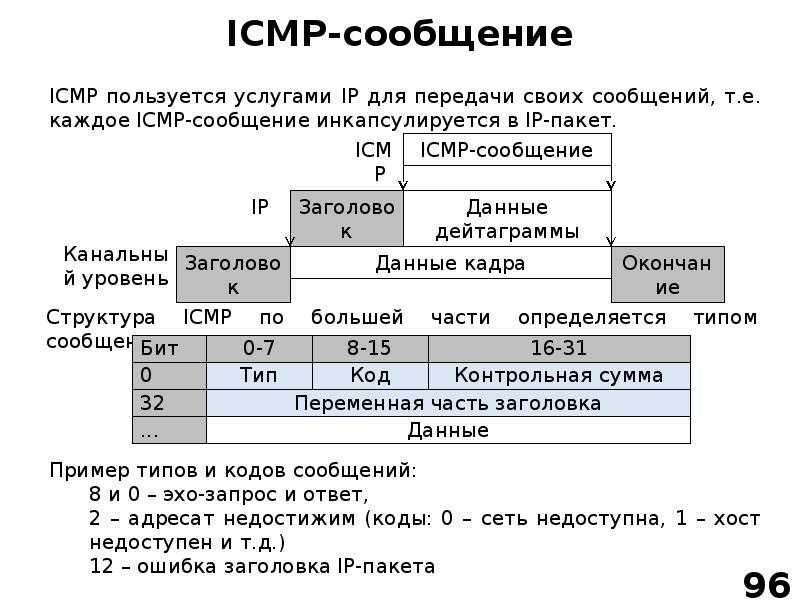 sh
sh
To make the script work as a service:
nano / nano / etc/systemd/system/pk.service
[Unit] Description=Start port-knocker [Service] StandardOutput=syslog StandardError=syslog WorkingDirectory=/opt/ Type=simple ExecStart=/bin/bash /opt/port-knocker.sh KillMode=process Restart=on-failure RestartSec=5s [Install] WANTEDBY = MULTI-USER.TARGET
Launch the script:
Systemctl Start PK
Systemctl Enable PK
Verkhov.s 999 -c1 MySRV.COM 9000 , that ports are open for such and such IP
Covert channel over ICMP
Covert channel over ICMP (ICMP tunnel) establishes a covert connection between two computers using ICMP echo request and echo reply packets. This technique allows, for example, full tunneling of TCP traffic via echo requests and responses (ping).
Author: Debasish Mandal
Introduction and Overview
A covert channel over ICMP (ICMP tunnel) establishes a covert connection between two computers using ICMP echo request and echo reply packets.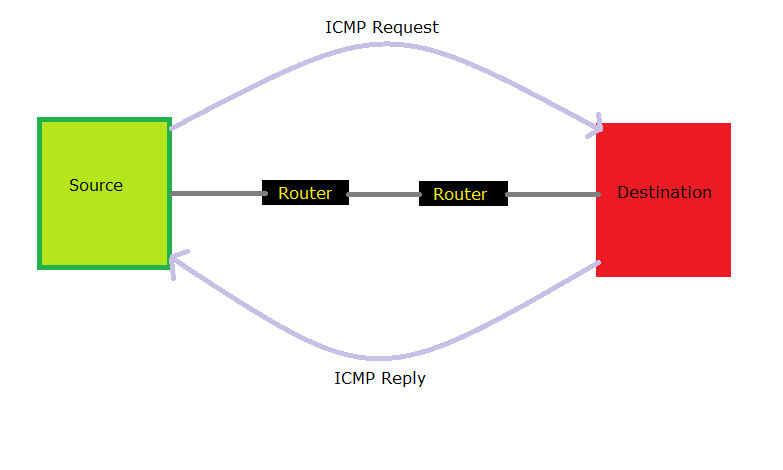 This technique allows, for example, full tunneling of TCP traffic via echo requests and responses (ping). Technically, tunneling through the ICMP covert channel occurs by injecting any desired data into an echo packet and forwarding it to a remote computer. The remote computer responds in a similar way by embedding the response in another ICMP packet and sending that packet back. nine0003
This technique allows, for example, full tunneling of TCP traffic via echo requests and responses (ping). Technically, tunneling through the ICMP covert channel occurs by injecting any desired data into an echo packet and forwarding it to a remote computer. The remote computer responds in a similar way by embedding the response in another ICMP packet and sending that packet back. nine0003
Some key points about ICMP
There are no ports in ICMP
We cannot ping ports. When someone talks about "pinging a port" they are really talking about using a layer four protocol (like TCP or UDP) to find out if a port is open. If someone pings port 80, it usually means that they are sending a TCP SYN packet to this system. Real ping works through the ICMP protocol, which does not use ports at all.
ICMP operates at the third layer. nine0108
Although ICMP sits "above" IP in the protocol stack, it is not a layer 4 protocol (considered to be another layer 3 protocol).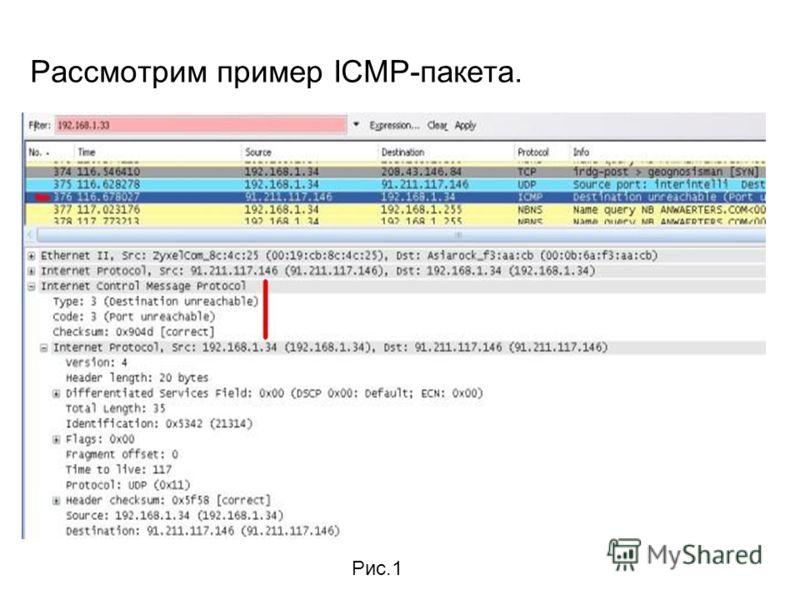
At the network layer, packets are routed based on a unique network address. The router acts like a post office, and the network layer stamps out letters (data) for transmission in a specific direction. The following protocols work at the network layer: IP, ICMP, ARP, RIP, OSI, IPX, and OSPF, as well as the following devices: router, bridge router, Frame Relay, and ATM switches. nine0003
Some key points about firewalls
Firewalls work at different levels to be able to apply different criteria to restrict traffic. The lowest level of firewall operation is the third. In the OSI model, it is called network. In the TCP/IP stack, this is the Internet Protocol layer. This layer is responsible for routing packets to their destination. At the third level, the firewall can tell if a packet comes from a trusted source, but it cannot tell what it contains or what other packets it is associated with. Firewalls that operate at the transport layer know a little more about the packet and can allow or deny access based on more complex criteria. At the application layer, firewalls have a lot of information about what's going on and can be very selective in granting access. nine0003
At the application layer, firewalls have a lot of information about what's going on and can be very selective in granting access. nine0003
It would seem that firewalls operating at higher levels of the protocol stack should be better at everything. This is not necessarily the case. The lower in the stack a packet is intercepted, the more secure the firewall provides. If an attacker cannot pass the third level, he will not be able to take control of the operating system.
Using an ICMP covert channel
ICMP tunneling can be used to bypass firewall rules by obfuscating the underlying traffic. Depending on the implementation of ICMP tunneling software, this type of connection can also be classified as an encrypted connection between two computers. Without deep packet inspection or review of system logs, network administrators will not be able to detect this type of traffic on their network. nine0003
Inside the ICMP packet
To see the contents of the ICMP packet, we will send requests to the remote host and listen for network traffic.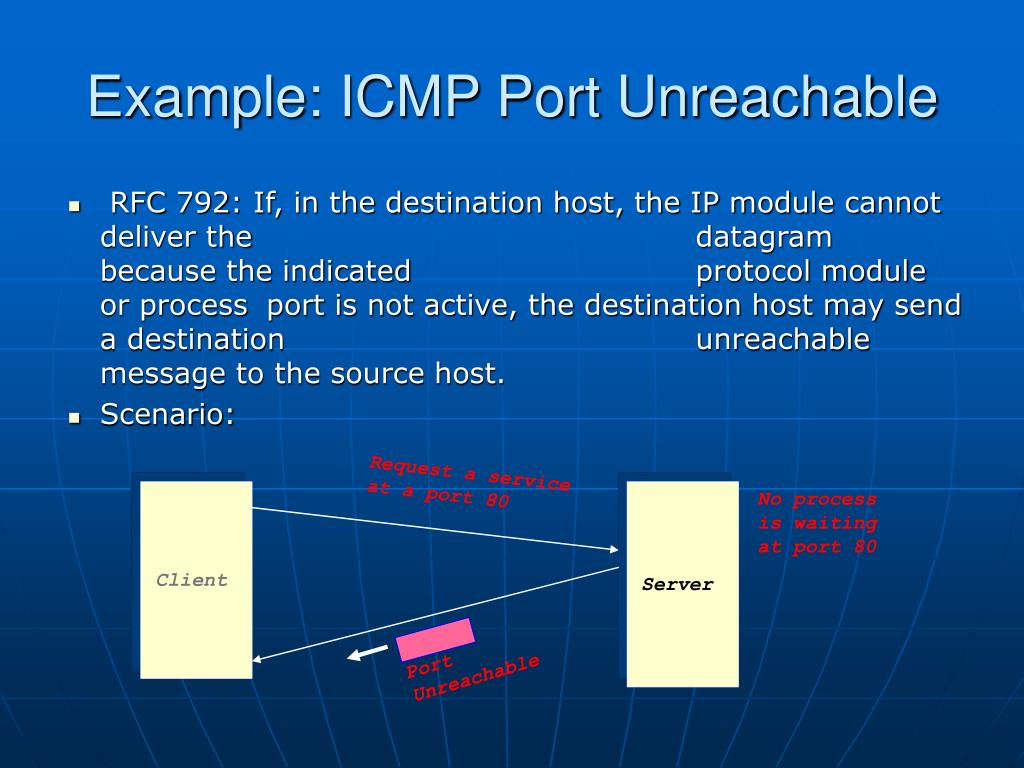
Let's take a look at normal ping.
Here we send normal ICMP echo requests to the remote host 192.168.157.1.
Capturing traffic with Wireshark, we will see the following:
Since we used the standard ping utility with no options, we sent several consecutive ICMP requests to the host. This will make it somewhat more difficult for us to analyze traffic. So let's send a single ICMP packet with no load. nine0003
The following command can be used for this purpose.
ping -c 1 -s 0
Now it will be easier to analyze the traffic.
In the sniffer on the remote host, we can see that 42 bytes of data have been received.
A typical ICMP packet structure is shown in the figure below.
Figure 1
Typical ICMP header structure:
Analyzing those 42 bytes of data, we can conclude that the first 14 bytes are an Ethernet header. nine0003
You can see that the first 12 bytes of the Ethernet header are nothing but the source and destination MAC addresses.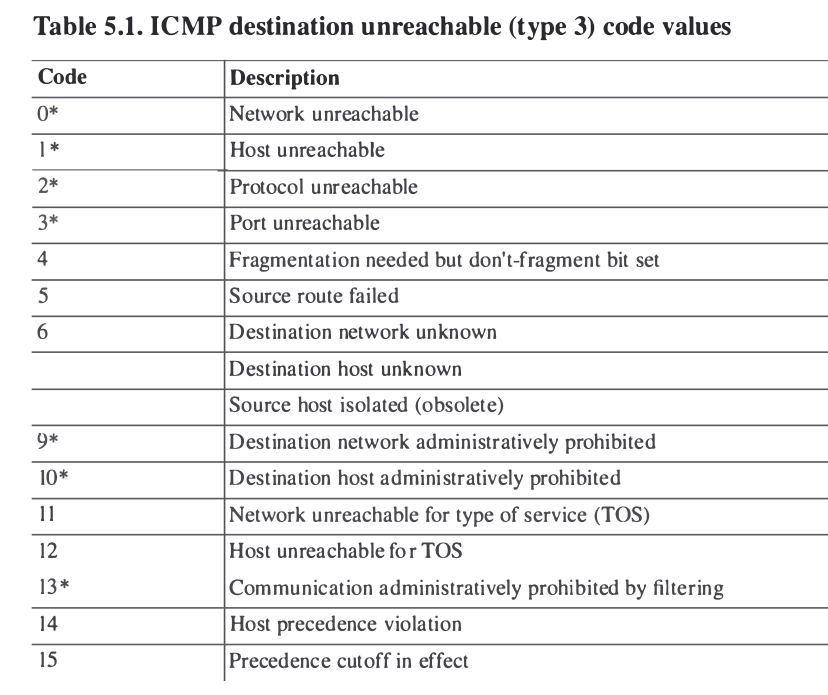
The next 20 bytes of the received datagram are the IP header (see Figure 1).
An IP header structure shown in more detail.
This is followed by 8 bytes of the ICMP header:
The structure of the ICMP header shown in more detail.
See also figure 2.
The ping utility, which is present in ordinary Linux systems, allows us to control the number of packets, their size, but does not allow us to form a special kind of echo request. Since our main goal is to manipulate the data in the contents of the ICMP packet, using the standard ping utility is not the best option.
HPING2
Hping is a free TCP/IP packet generator and analyzer distributed by Salvatore Sanfilippo (also known as Antirez). With hping, we can also manipulate the data portion of a single ICMP packet. Using hping, we will send a single ICMP packet again, but this time we will add some garbage to it. nine0003
In the screenshot, you can see that we added 4 “A” characters to the packet and sent it to the address 192. 168.157.1.
168.157.1.
Let's listen and analyze the traffic.
Now you can see that we have captured 46(42+4) bytes of data. In the screenshot, it is easy to distinguish our load, consisting of highlighted "41". This is the hex representation of the character "A".
DIY PING: Life is short so I prefer Python.
In the above examples, we used the standard ping utility and the hping utility to send ICMP echo requests to any host. We now use Python to send a homemade ICMP packet. nine0003
In this case, we form not only the ICMP header and packet stuffing, but also the headers of the Ethernet and IP protocols.
The "dump" variable in the above script contains the entire datagram, including the Ethernet header, IP header, ICMP header, and stuffing. Here, four “A” characters (\x41\x 41\x 41\x 41) act as filling.
It is clear from the above that we can easily send arbitrary data to an arbitrary host by embedding the data in an echo packet. Now all that's left is to run a daemon on the remote host that can respond in this way by embedding the response in another ICMP packet and sending the packet back. nine0223
Now all that's left is to run a daemon on the remote host that can respond in this way by embedding the response in another ICMP packet and sending the packet back. nine0223
Putting it all together
To do this, we need to programmatically implement the following steps:
- The daemon listens for ICMP packets
- After receiving the packet, its stuffing is extracted (correct request from the attacker)
- Based on the filling, the necessary actions are taken
- Reverse ICMP packet is sent with response
I wrote a simple ICMP tunneling server and client in Python that allows you to establish a covert channel between two hosts. nine0003
Server ID:
http://pastebin.com/JLD6grb2
Client ID:
http://pastebin.com/gh4zzHdQ
This covert channel daemon essentially receives OS commands from ICMP packets and runs these commands on a remote host by sending ICMP response packets with the results of command execution. As soon as the daemon is started on the host, it starts listening for ICMP packets. After receiving commands from the client, it extracts the stuffing from the packets and runs the command on its host, sending back an ICMP packet with the result. If the command output is too long, the daemon will send it in multiple packets. nine0003
As soon as the daemon is started on the host, it starts listening for ICMP packets. After receiving commands from the client, it extracts the stuffing from the packets and runs the command on its host, sending back an ICMP packet with the result. If the command output is too long, the daemon will send it in multiple packets. nine0003
The client-side sniffer receives response packets and extracts the command output from the stuffing. After parsing, it displays the output. The Hping utility can also be used as a client for this daemon. In this case, the filling should be formed according to a certain pattern so that the daemon can recognize the request. Then, to parse the response, you should use a client script, or Wireshark.
Video demonstration of this covert channel:
A few other well-known covert channel utilities:
LOKI
LOKI is a program for tunneling information. It uses echo reply packets as payload carriers.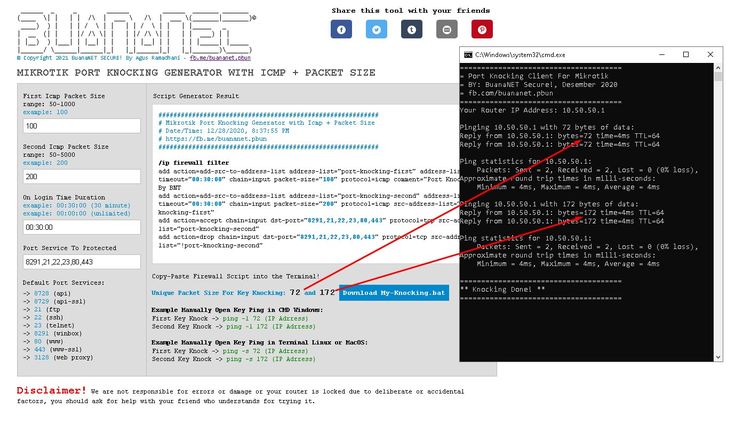
NCovert
Performs covert file transfer by hiding transferred files in seemingly harmless data using packet forgery. In some cases, it allows you to hide the real IP address of users.
007 Shell
007 Shell is a simple client-server program written in C for remote system administration over a network using techniques similar to those used by Loki. Commands and response messages are encapsulated in the payload of ICMP ECHO_REPLY packets (echo reply packets). nine0003
ICMPTX (IP-over-ICMP):
ICMPTX is a program that allows a root user to create a virtual network connection between two computers by hiding data inside ICMP packets.
Ways to fight
Trying to prevent covert channels is like chasing a cat by a dog. You can only prevent certain channels if you are aware of them, you can analyze the traffic they generate, and then configure your IDS accordingly (for example, write Snort rules). However, when covert channels generate different traffic with each packet (for example, using bit-flipping) or use advanced timing techniques, it becomes impossible to prevent them.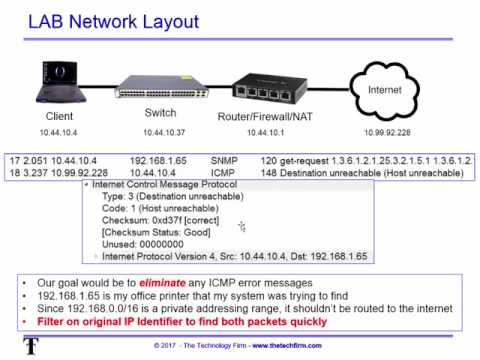 nine0003
nine0003
Although the only way to prevent this type of tunneling is to completely block ICMP traffic, this is not feasible for real world production environments. One method of combating this type of attack is to allow only fixed-sized ICMP packets through the firewall to virtually eliminate this type of behavior. The IDS can treat large ICMP packets as suspicious and raise an alarm. However, since there are legal ways to use large ICMP packets, it is difficult to determine whether a large ICMP packet is actually malicious. For example, large ICMP packets are used to test whether large packets can be sent over the network. Distinguishing legal packets from illegal ones is even more difficult if the covert channel is encrypted. The IDS must be able to determine if a packet is encrypted. Distinguishing encrypted from unencrypted packets is still an open problem for research. nine0003
Snort provides one or two rules that can help detect ICMP covert channels. Another possibility is to detect the "Dont Fragment" bit in the covert channel, and so on.