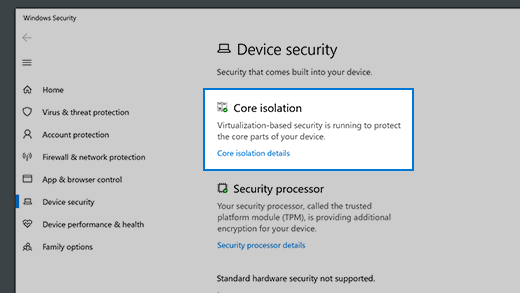
Device protection in Windows Security
Windows 10 Security More…Less
Windows Security provides built-in security options to help protect your device from malicious software attacks.
To access the features described below, tap the Windows Start button, type windows security, select it from the results, and then select Device security.
Notes: What you actually see on the Device security page may vary depending upon what your hardware supports.
-
For more info about Windows Security, see Stay protected with Windows Security.
-
For more info about Microsoft Defender Firewall, see Turn Microsoft Defender Firewall on or off.
- Features and Benefits
Vast Ecosystem
More than 1,000 software, tools and service partners to support and enable the use of our technology.
Standard Industry Framework
The Arm Platform Security Architecture (PSA) is the framework for a common security best practice.
Protection Against a Broad Spectrum of Attacks
Our IP extends across the system with protection for processors, subsystems, acceleration, and offloading—all fitting together seamlessly for layered protection.
Always Expanding
Arm continues to build on its history in mobile security, addressing new market requirements for developer-friendly, deterministic, real-time embedded and IoT applications.
Security IP
Arm provides an expanding portfolio of secure IP, firmware and software, collaborating with the ecosystem to provide the right counter-measures for the variety of threats now facing devices.
Arm CryptoCell Family
Arm CryptoCell enables the protection of assets (code and data) belonging to different stakeholders in an ecosystem (for example, silicon vendor, OEM, service provider, user). CryptoCell enables SoC designers to trade off area, power, performance or robustness in a very flexible manner so that SoC designs can be optimized to achieve the most appropriate security level for the target market.
- CryptoCell-300 Family
- CryptoCell-700 Family
Physical Security Solutions
Arm’s suite of physical security solutions empowers designers to build in the necessary physical protection at the heart of the device.
 The suite includes both processor IP equipped with tamper resistance, plus a range of IP specifically created to mitigate side-channel attacks.
The suite includes both processor IP equipped with tamper resistance, plus a range of IP specifically created to mitigate side-channel attacks.- Cortex-M35P
- SecurCore SC300
- SecurCore SC000
- Physical Security Solutions
TrustZone Technology for Processor IP
Arm TrustZone technology is a system-on-chip (SoC) and CPU system-wide approach to security with hardware-enforced isolation to establish secure end points and a device root of trust.
- TrustZone for Cortex-A Processors
- TrustZone for Cortex-M Processors
TrustZone Security System IP
Arm also has a range of Security System IP to provide multiple layers of processor and data protection.
- TrustZone Random Number Generator
- TrustZone Full Disk Encryption
- TrustZone Address Space Controllers
Talk with an Expert
Our security expert team is here to help you.

Contact Us
Securing the Next One Trillion Devices
Arm-based chips are already in more than 100 billion devices, and as the Internet of Things (IoT) rapidly expands, we expect that number to grow to a global network of one trillion connected devices. Security cannot be an afterthought. It must considered at inception, and each threat addressed with the appropriate countermeasure. Arm has been helping the ecosystem secure devices from chip to cloud for many years, and remains committed to an end-to-end approach to security.
Learn More
Build a Secure IoT System-on-Chip
Designing a secure system-on-chip (SoC) is challenging and time-consuming. It involves defining a system architecture, acquiring the right IP and integrating many pieces of IP together to build a system that perfectly matches your requirements.
Arm Corstone helps SoC designers build secure systems faster and is the perfect starting point for your SoC, with reference packages that include a pre-verified subsystem that can be tailored to your specific needs.

Learn More
Intel vs AMD Processor Security: Who Makes the Safest CPUs?
The multi-decade long fight between Intel and AMD has recently taken a new dimension, as more users begin to wonder which processors can protect their computers, data, and online activities best.
(Image credit: Shutterstock)
Up until the last few years, both regular users and cyber security researchers were mostly worried about the plethora of software vulnerabilities for which there never seems to be an end in sight.
However, at the beginning of January 2018, many users and security researchers realized that the hardware powering our devices is not nearly as secure and free from serious security issues as we once thought.
That leaves us with the question: Which company is more secure? The question might seem pedantic when we consider that Intel currently has 242 publicly disclosed vulnerabilities, while AMD has only 16 (a 15:1 difference in AMD’s favor), but both companies also have a full roster of special security-minded features.

2018: Year “Zero” In Processor Security
In January 2018, Google’s Project Zero security experts, as well as other independent security researchers, disclosed the Meltdown and Spectre CPU design flaws . These vulnerabilities existed because of the design choice most CPU architecture teams have made to increase the performance of their chips.
The Meltdown flaw, also called Spectre variant 3, affected both Intel and ARM CPUs. It allowed third-party code to break down the isolation between applications and the operating system that is normally enforced by hardware. Attackers can use this to access the memory of other applications and the operating system, thus allowing them to steal secrets.
The Spectre vulnerability breaks the security boundary between different applications, making even those applications that follow best coding practices become vulnerable to attackers that exploit this side-channel security hole in PCs.
Spectre affects virtually all out-of-order CPUs that use speculative execution to increase performance, including AMD and Arm’s processors.
 However, newly discovered side-channel attacks from the Spectre family seem to affect Intel more than the other two vendors, which implies that Intel may have taken more liberties with its CPUs than its competitors to keep the performance edge.
However, newly discovered side-channel attacks from the Spectre family seem to affect Intel more than the other two vendors, which implies that Intel may have taken more liberties with its CPUs than its competitors to keep the performance edge.Speculative execution is a CPU design feature that allows a CPU to work on some tasks that may or may not be needed next. If these tasks are needed, then they are more easily accessed when needed, and thus the performance of the CPU increases compared to if this feature didn’t exist.
This is also why although specific variants of Spectre can be fixed in software or can even be mitigated in hardware, new variants will keep being discovered by researchers until the CPU makers decide enough is enough and disable the speculative execution feature altogether, or design entirely new architectures.
This isn’t just a theory, and it has already happened several times since the original disclosure of the Meltdown and Spectre flaws (in less than two years).

Mere months after researchers revealed Spectre, another group of security researchers prepared to disclose “Spectre Next Generation” family of new speculative-execution flaws. Intel allegedly attempted to delay the disclosure, as the company had already taken a big PR hit earlier that year with the first Spectre reveal.
Speculative execution has created at least two other bugs, Foreshadow and Zombieload, that essentially make Intel’s Hyper-Threading technology insecure. OpenBSD founder Theo de Raadt has warned against keeping Hyper-Threading enabled on Intel machines from the start.
It wasn’t until the latest Zombieload attack that other OS vendors such as Google and even Apple joined the OpenBSD founder on this. Google disabled Hyper-Threading on all Chromebooks , while Apple noted only that the full mitigation of Zombieload and other Microarchitectural Data Sampling (MDS) vulnerabilities would require disabling Hyper-Threading, leaving it as an option for users .
Intel itself has also recommended disabling Hyper-Threading but only to some customers “who cannot guarantee that trusted software is running on their system(s).” However, with virtually everyone running other people’s software on their PCs or servers, who can really tell what’s trusted and what isn’t?
Attack Surface
The vast majority of speculative execution attacks don’t impact AMD’s processors, with a few exceptions such as Spectre variants 1, 1.1, and 4, the latter of which is called Speculative Store Bypass .
AMD CPUs were also impacted by PortSmash, a vulnerability affecting its Simultaneous Multi-Threading (SMT) feature, which is similar to Intel’s Hyper-Threading. AMD processors were also vulnerable to NetSpectre and SplitSpectre, as these vulnerabilities affected processors, that were also vulnerable to Spectre v1.
AMD’s processors were susceptible to Spectre variant 2 and the company issued an update for it, but it said the vulnerability was “difficult to exploit due to our architecture.
 ”
” AMD’s chips were also affected by five out of seven new Meltdown and Spectre attacks found by a group of researchers that included some of the original researchers that discovered the original Spectre and Meltdown design flaws. Intel’s chips were susceptible to all seven vulnerabilities.
AMD’s CPUs, including the latest Ryzen and Epyc processors, are immune to:
- Meltdown (Spectre v3)
- Spectre v3a
- LazyFPU
- TLBleed
- Spectre v1.2
- L1TF/Foreshadow
- SPOILER
- SpectreRSB
- MDS attacks (ZombieLoad, Fallout, RIDL)
- SWAPGS
As we can see, AMD’s CPUs seem to have significantly higher resiliency against speculative execution attacks compared to Intel’s processors. However, flaws that are highly similar to Spectre v1 seem to continue to affect AMD’s processors, too. The good news is that in most cases, the original Spectre v1 firmware mitigation can also protect against these new flaws.
Both Intel and AMD have issued firmware and software patches for all of the flaws mentioned above although not all of them may have arrived to users if the updating process depended on the motherboard or device makers and not on Intel/AMD, or on the OS vendors such as Microsoft, Apple, etc.

Winner: AMD
Performance Impact Of Spectre Software Mitigations
The chipmakers had roughly six months warning about the original Spectre and Meltdown flaws before the public learned about them. This created its own controversy, as not all OS vendors learned about them at the same time. Some were given days or weeks to deal with the bugs.
Even with a six-month head-start, the initial fixes caused quite a few issues on people’s computers from significantly slowing down performance to causing them to crash. Things improved somewhat with some updates a few months down the road.
However, even if those patches were optimized to minimize the performance loss , it became quite difficult for the chipmakers — Intel especially — to deal with the patching all of the Spectre-class vulnerabilities while still minimizing the performance overhead of the patches.
According to a recent report, all the patches Intel has had to deliver have slowed down users’ PCs and servers about five times more than AMD’s own patches.
 That’s a significant gap, and it’s primarily because Intel has had to fix many more security holes than AMD.
That’s a significant gap, and it’s primarily because Intel has had to fix many more security holes than AMD.Winner: AMD
(Image credit: Shutterstock)
(Some) Hardware Mitigations Against Side-Channel Attacks
Perhaps because of so many firmware and software mitigations Intel had to issue for Spectre-class security flaws, the company also changed its mind about adding hardware-based mitigations to its processors. Intel was initially somewhat reluctant to do that, or at least to add significant changes to its architecture. However, it later committed to a “security-first” principle .
In some ways, the company has lived up to that commitment. Intel has included hardware mitigations for Meltdown and Foreshadow, as well as partial MDS hardware mitigation in some of its most recent CPUs, starting with select Whiskey Lake and Cascade Lake processors .
The company also promised a hardware fix for Spectre v2 is in the works and has implemented a fix that uses both in-built hardware and software.
Intel and AMD haven’t fixed Spectre v1, the most dangerous speculation execution attack, in hardware, yet. However, both AMD and Intel have patched Spectre v1 at the software level.
In some cases, Intel has also allegedly ignored, downplayed, or delayed the disclosure of some of the Spectre-class vulnerabilities. In the case of the MDS attacks, Intel allegedly wanted to donate up to $80,000 to the researchers if they downplayed the severity of the MDS attacks. The academics rejected the offer.
It’s not clear whether or not Intel is purposefully avoiding fixing Spectre v1 and other side-channel attacks in hardware because it’s expensive and it could break too many things, or if the company is just biding time until it’s ready to release such a processor.
One thing seems clear, and that is the fact that software patches for speculative execution side-channel attacks will not be enough to prevent similar new attacks from appearing. Academics are skeptical that trying to patch-up the architecture is going to result in long-term security benefits over an architecture design change.
Therefore, if Intel, AMD, and other chipmakers are unwilling to change the design of their CPU architectures, we may be stuck with Spectre-class side-channel attacks forever .
(Image credit: Intel — Edited)
There is some movement on patching some vulnerabilities with in-silicon fixes, though. Intel has added new hardware-based mitigations for many of the new vulnerabilities, like MSBDS, Fallout, and Meltdown, with new steppings of its die. Intel is quietly releasing a cadence of new steppings with its 9th-Gen Core processors that add more hardware-boosted mitigation capabilities to already-shipping models. These in-built mitigations are designed to ease the performance overhead of software-based Windows security patches.
Meanwhile, AMD hasn’t added any new in-silicon mitigations to its already-shipping chips, though it is working them into newer models. However, it bears mentioning that AMD simply doesn’t require as many alterations to fend off vulnerabilities as Intel, so it doesn’t require the sheer breadth of hardware-based fixes.
 As such, we’re calling this one in favor of AMD.
As such, we’re calling this one in favor of AMD. Winner: AMD
Intel’s ME and Other Security Vulnerabilities
Before the Spectre flaws became known, and even afterward, the biggest privacy or security-related issue with Intel’s chips revolved around Intel’s built-in Management Engine. However, the speculative execution side-channel flaws overshadowed all the other security vulnerabilities, even though other vulnerabilities may have been just as important.
In 2017, Intel confirmed a security bug in ME that would have allowed attackers to exploit the firmware remotely and take over any Intel-powered machine. The bug affected all processors since 2008.
Later in 2017, researchers found another ME flaw that affected processors from Skylake in 2015 to Coffee Lake in 2017. This one allowed ME to remain active, even if ME could be disabled through unofficial means, as users can’t normally disable ME.
Positive Technologies security researchers found a way to disable Intel ME that same year through an undocumented mode that Intel secretly implemented for government authorities.
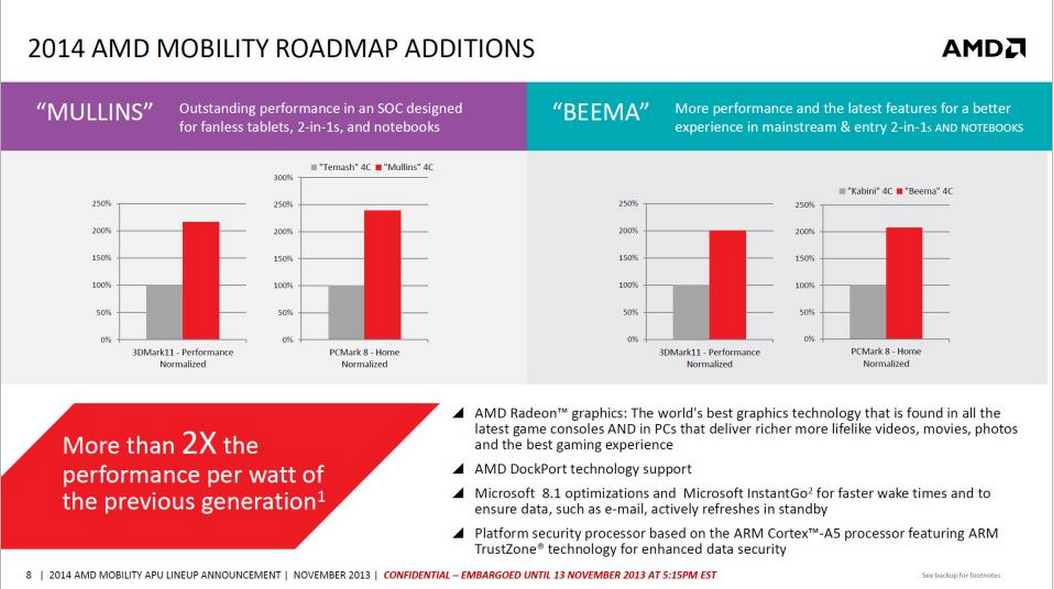 Intel supposedly did this to allow the NSA and other government authorities to disable potentially vulnerable functionality of the ME that would affect everyone else in the PC market.
Intel supposedly did this to allow the NSA and other government authorities to disable potentially vulnerable functionality of the ME that would affect everyone else in the PC market.Researchers also found two new sets of ME security bugs in 2018 while Intel was deep into dealing with the Spectre aftermath.
Due to fears that ME could either be an “official” backdoor or that it could be used like one by malicious parties, some computer makers such as Purism, Systems 76, and even Dell have started offering laptops with ME disabled by default. Google has also started disabling ME for some of its internal devices.
At the time of this writing, there are 242 publicly disclosed Intel firmware vulnerabilities.
AMD’s PSP, Ryzenfall, Chimera & Other CPU Flaws
The AMD Platform Security Processor (PSP), also known as AMD Secure Processor, uses an Arm Cortex-A5 processor to isolate certain chip platform functions from the main processor and the main operating system.
 It’s similar to AMD’s ME, and just like ME, it can also be potentially exploited to devastating effect if a malicious party finds a bug in it.
It’s similar to AMD’s ME, and just like ME, it can also be potentially exploited to devastating effect if a malicious party finds a bug in it.Since 2017, at least three PSP vulnerabilities have been found. A Google security researcher found one in 2017. The bug would have given attackers access to passwords, certificates, and other sensitive information.
Other PSP bugs were found in 2018, along with the disclosure of 13 security flaws in total that affected AMD’s Zen-based processors. The researchers placed them into four categories: Ryzenfall, Chimera, Fallout, and Masterkey .
According to the researchers, the Ryzenfall bugs would have allowed attackers to take full control of the AMD Secure Processor. When combined with the bugs classified as Masterkey, the attackers would have also been able to install persistent malware on targets’ machines.
The Chimera bugs involved the existence of two manufacturer ASMedia chipset backdoors , one found in the firmware and the other in the hardware (ASIC) of the chipset.
 The backdoors allowed the injection of malicious code into the Ryzen chipset.
The backdoors allowed the injection of malicious code into the Ryzen chipset. The Fallout flaws allowed attackers to read and write to protected memory areas, such as SRAM and Windows Credential Guard isolated memory.
AMD has mostly downplayed these bugs, saying that in most cases, the attackers would need physical access to the machines to exploit those security vulnerabilities. However, in the CVE Details database we can see that most of them have a very high severity rating:
(Image credit: Tom’s Hardware)
AMD has issued patches to all OEMs and ODMs whose hardware was affected by the bugs, but as usual, it’s up to those companies to patch users’ computers, which makes support spotty.
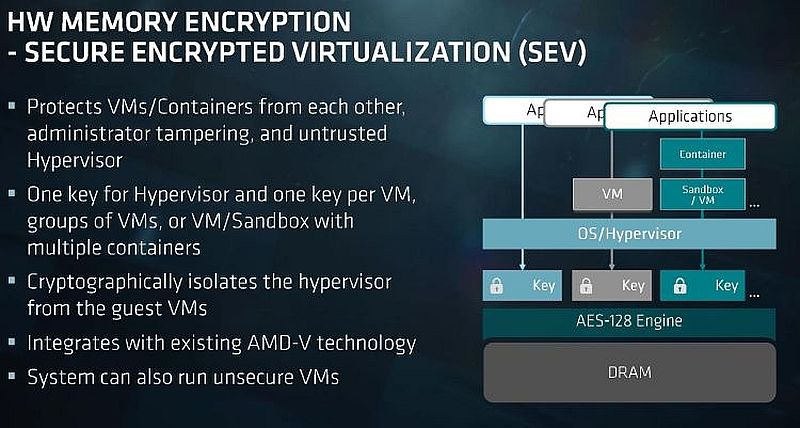
Researchers have also found AMD’s Secure Encrypted Virtualization (SEV) feature for Epyc server chips to be insecure on occasion. The first SEV vulnerability was announced as part of the Masterkey disclosure mentioned earlier. The researchers said that the Masterkey bugs could be exploited to tamper with the security of SEV as well as that of the firmware Trusted Platform Module (fTPM).

Another group of researchers disclosed a second SEV vulnerability, called SEVered , just a few months later in May 2018. The bug could have allowed attackers to remotely extract memory contents of a virtual machine that would normally be protected by SEV.
A Google researcher found the most recent SEV vulnerability earlier this year. Once again, it involves a bug that allows attackers to extract the encryption keys used by the SEV feature to encrypt the memory contents of the protected VMs.
In other words, this is the third time in about a year that SEV was proven to fail at doing its job — that of protecting VM memory. This doesn’t necessarily put Intel’s similar SGX feature in a better position, as it was also found to have several weaknesses caused by the Spectre-family side-channel CPU flaws .
Winner: Tie
Best Intel CPU Security Features
It’s not all bad news when it comes to the security of modern processors. Although it is still an emerging initiative, Intel committed to prioritizing security above else after researchers disclosed the first Spectre flaws.

As mentioned earlier, the company has already promised some mitigations for Spectre vulnerabilities in hardware, and a number of them have already landed in current-gen processors.
However, in the end these are just small fixes to something that shouldn’t have been broken in the first place, and we’re looking for security beyond fixing broken architectures. So what else do Intel processors have to offer in regards to user security?
(Image credit: Shutterstock)
Intel SGX
Software Guard eXtensions is perhaps Intel’s most popular and most advanced processor security feature it has released in recent years. SGX enables applications to store sensitive data such as cryptographic keys in a secure virtual enclave inside hardware-encrypted RAM that the main operating system or other third-party applications can’t access. Applications such as the end-to-end encrypted Signal messenger make use of it so that it can pair users to each other securely and privately.
Intel TME/MKTME
Intel recently also announced plans to evolve SGX so that it can offer Total Memory Encryption (TME), instead of encrypting only a small portion of memory as SGX does.
 The new feature is actually two features in one: TME offers a single encryption key for all memory, while another variant called Multi-Key Total Memory Encryption offers — you guessed it — full memory encryption with support for multiple keys, such as one key per encrypted VM.
The new feature is actually two features in one: TME offers a single encryption key for all memory, while another variant called Multi-Key Total Memory Encryption offers — you guessed it — full memory encryption with support for multiple keys, such as one key per encrypted VM. MKTME enables encryption in memory, at rest, as well as in transit. As Intel’s feature arrives a little later than AMD’s, perhaps the company has learned from its competitor’s mistakes with SEV, as well as its own with SGX.
Hardware memory encryption would give users a significant security benefit because it should make it much more difficult for applications to steal data from others in the future (granted the operating systems also put significant restrictions on the APIs that allow apps to share data). However, it’s not clear yet whether Intel and AMD intend to leave this feature to enterprise customers or if they’ll enable then for mainstream users, too.
Best AMD CPU Security Features
AMD may have been late to the memory encryption game, as Intel beat the company to it with the launch of SGX.
 However, when AMD launched the Ryzen processors, these came out both with Secure Memory Encryption (SME) and with Secure Encrypted Virtualization (SEV), features that were, and still are, significantly more advanced than Intel’s.
However, when AMD launched the Ryzen processors, these came out both with Secure Memory Encryption (SME) and with Secure Encrypted Virtualization (SEV), features that were, and still are, significantly more advanced than Intel’s.AMD SME
The SME feature is typically enabled in the BIOS or other firmware at boot time. It provides page-granular memory encryption support using a single ephemeral 128-bit AES encryption key generated via a hardware random number generator. SME enables applications to mark certain memory pages they use for encryption.
These pages are then automatically encrypted and decrypted when the application needs to read or write that data. The feature protects against physical attacks meant to steal sensitive customer data that still resides in plain-text RAM.
AMD TSME
AMD’s Transparent SME is a stricter subset of SME that encrypts all memory by default and doesn’t require applications to support it in their own code. It’s especially more useful for legacy applications that can no longer be expected to modify their code, but they can still benefit from encryption of the data they process.
AMD seems to have recently re-branded TSME to “Memory Guard” and included it as part of GuardMI for the company’s new Ryzen Pro 3000 CPUs . GuardMI is AMD’s alternative to Intel’s vPro, which includes both manageability and security features for enterprise customers. One feature AMD has over Intel right now is Memory Guard, which protects a system’s data against cold boost attacks.
AMD SEV
AMD’s SEV is an extension of SME that encrypts the memory of each VM with its own ephemeral encryption keys. This way, the VMs can stay completely isolated from each other. AMD came up with the idea while working on security features for Sony and Microsoft’s consoles .
In practice, SEV, like Intel’s SGX, can still prove vulnerable to side-channel attacks or other exploits that gain access to the encryption keys. Both AMD and Intel still have much work to do in terms of ensuring these features are close to invulnerable to attacks.
Winner: AMD
(Image credit: AMD)
Why Processor Security Matters
Why should you even care about processor security? Aren’t the Windows, macOS, or Linux security features enough? The answer is: no, they are not enough, and yes, even you could be affected by these bugs.
 It’s not just data center and web hosting companies that need to worry about these attacks.
It’s not just data center and web hosting companies that need to worry about these attacks.First off, the hardware runs at a level below the operating system. Another way of putting it is that the hardware gets to control what the software on top of it ultimately does. Therefore, if anyone takes over hardware, it means they can now control what the operating system and applications do, too. This includes the attackers having control over how those security features work or disabling these features altogether.
Second, even if nobody will attempt to target you by name online, you could still be a victim of a mass-infection of malware that gets spread through advertising networks, hacked sites you visit, internal networks at work, and so on. The hardware exploits could be part of an entire chain of exploitation tools that have on main goal: steal the data of anyone they come across.
If you can’t guarantee the security of the hardware in your device, then all the security features of your favorite operating system or applications are basically irrelevant.
 For instance, this is why Apple and Google have begun building their own servers or have stopped buying from less trustworthy server hardware providers. The two companies implement top-notch security as far as their software goes, but if there is a backdoor in the hardware they use, none of that matters.
For instance, this is why Apple and Google have begun building their own servers or have stopped buying from less trustworthy server hardware providers. The two companies implement top-notch security as far as their software goes, but if there is a backdoor in the hardware they use, none of that matters.Intel vs AMD Processor Security: Conclusion
In the short-to-medium-term, it’s probably going to get worse before it gets better for both AMD and Intel’s processors, despite the two companies’ best efforts. Yes, we’ll likely get some more hardware mitigations — perhaps just enough to appease a large portion of consumers and media, but not quite enough to solve all the issues due to all the difficulties and costs involved in turning major processor architectures around.
We should also get some interesting new security features in the coming years from both Intel and AMD. But the next few years will likely be dominated by more reports of security vulnerabilities found in both the companies’ processors as more researchers start digging deeper into their CPU microarchitectures.
It’s also going to take the two companies years to fix the flaws the researchers found with new architecture designs. In the end, it should all be for the better as it will force processors to become more mature.
But the question remains, who makes the most secure processors right now that keep you the safest online? We can debate about whether or not researchers took a better look at Intel’s flaws because its chips are much more popular, but at the end of the day a few things are undeniable:
1) Intel currently has 242 publicly disclosed vulnerabilities, while AMD has only 16. That’s a 15:1 difference in AMD’s favor. The gap is just too large to ignore.
2) Less than half of the speculative execution side-channel attacks disclosed for Intel since early 2018 seem to affect AMD’s Ryzen and Epyc CPUs. It’s true that in some of the cases where the flaws were declared to affect Intel’s CPUs, the researchers may not have looked primarily at AMD’s CPUs. However, even then AMD confirmed that those bugs didn’t affect its processors after carefully verifying how the vulnerabilities affected its own processors.
 It truly seems as if AMD designed the new Ryzen microarchitecture with better security in mind than Intel’s essentially Nehalem-based microarchitectures have been. Why Nehalem-based? Because most of the speculative execution attacks affect Intel’s CPUs since at least 2008 when the Nehalem microarchitecture came out.
It truly seems as if AMD designed the new Ryzen microarchitecture with better security in mind than Intel’s essentially Nehalem-based microarchitectures have been. Why Nehalem-based? Because most of the speculative execution attacks affect Intel’s CPUs since at least 2008 when the Nehalem microarchitecture came out.3) With the release of the new Zen architecture, AMD also seems to have been one step ahead of Intel in terms of supporting new hardware encryption features. It remains to be seen if AMD will maintain this pace in regards to security, as Intel tries to fix all of the Spectre issues and improve its image with consumers, but at least for now, AMD seems to have the lead.
Even ignoring all the various performance slowdowns the Spectre-related patches have caused for both old and new systems alike, AMD’s processors seem like the safer and more secure platform to choose in the near and medium-term.
Intel AMD Attack Surface ✗ Performance Impact ✗ Hardware Mitigations ✗ Other CPU Flaws ✗ ✗ Best Security Features ✗ Total 1 5 MORE: Best CPUs
MORE: Intel & AMD Processor Hierarchy
MORE: All CPUs Content
Lucian Armasu is a Contributing Writer for Tom’s Hardware US.
 He covers software news and the issues surrounding privacy and security.
He covers software news and the issues surrounding privacy and security.Meltdown and Spectre
Vulnerabilities in modern computers leak passwords and sensitive data.
Meltdown and Spectre exploit critical vulnerabilities in modern processors.
These hardware vulnerabilities allow programs to steal data which is currently processed on the computer.
While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs.
This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents.Meltdown and Spectre work on personal computers, mobile devices, and in the cloud.
Depending on the cloud provider’s infrastructure, it might be possible to steal data from other customers.
Meltdown
Meltdown breaks the most fundamental isolation between user applications and the operating system.
This attack allows a program to access the memory, and thus also the secrets, of other programs and the operating system.If your computer has a vulnerable processor and runs an unpatched operating system, it is not safe to work with sensitive information without the chance of leaking the information. This applies both to personal computers as well as cloud infrastructure. Luckily, there are software patches against Meltdown.
Spectre
Spectre breaks the isolation between different applications.
It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets.
In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to SpectreSpectre is harder to exploit than Meltdown, but it is also harder to mitigate.

However, it is possible to prevent specific known exploits based on Spectre through software patches.Who reported Meltdown?
Meltdown was independently discovered and reported by three teams:
- Jann
Horn (Google Project Zero), - Werner Haas, Thomas Prescher (Cyberus Technology),
- Daniel Gruss, Moritz Lipp, Stefan Mangard, Michael Schwarz (Graz University of Technology)
Who reported Spectre?
Spectre was independently discovered and reported by two people:
- Jann
Horn (Google Project Zero) and - Paul Kocher in collaboration with, in alphabetical order,
Daniel Genkin (University of Pennsylvania and University of Maryland), Mike Hamburg (Rambus), Moritz Lipp (Graz University of Technology), and Yuval Yarom (University of Adelaide and Data61)
Am I affected by the vulnerability?
Most certainly, yes.
Can I detect if someone has exploited Meltdown or Spectre against me?
Probably not. The exploitation does not leave any traces in traditional log files.
Can my antivirus detect or block this attack?
While possible in theory, this is unlikely in practice. Unlike usual malware, Meltdown and Spectre are hard to distinguish from regular benign applications. However, your antivirus may detect malware which uses the attacks by comparing binaries after they become known.
What can be leaked?
If your system is affected, our proof-of-concept exploit can read the memory content of your computer. This may include passwords and sensitive data stored on the system.
Has Meltdown or Spectre been abused in the wild?
We don’t know.
Is there a workaround/fix?
There are patches against Meltdown for Linux ( KPTI (formerly KAISER)), Windows, and OS X.
There is also work to harden software against future exploitation of Spectre, respectively to patch software after exploitation through Spectre ( LLVM patch, MSVC, ARM speculation barrier header).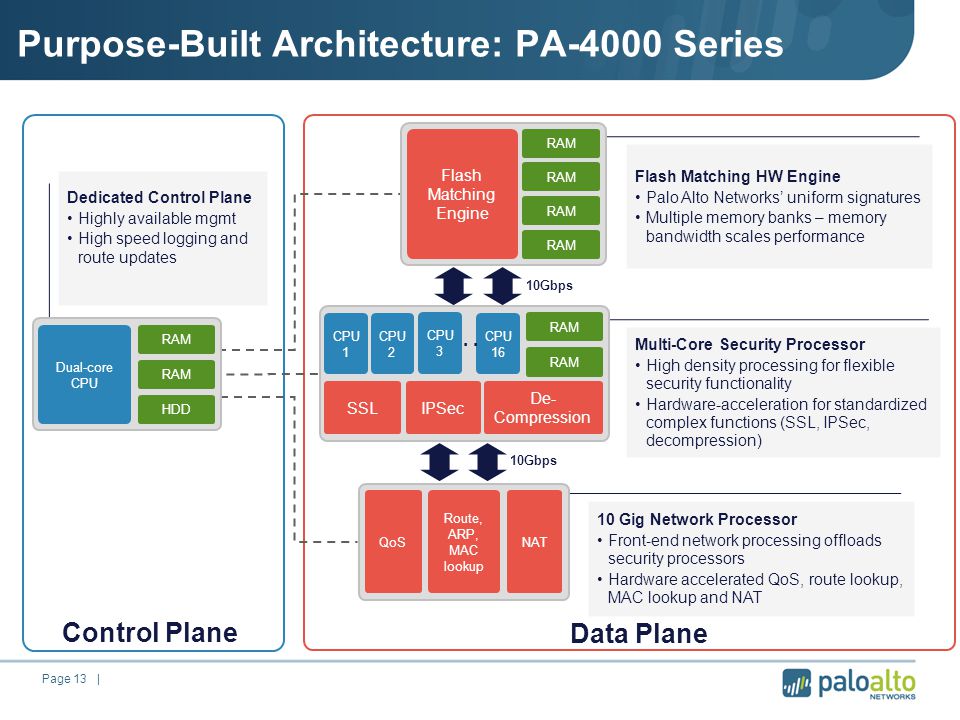
Which systems are affected by Meltdown?
Desktop, Laptop, and Cloud computers may be affected by Meltdown. More technically, every Intel processor which implements out-of-order execution is potentially affected, which is effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). We successfully tested Meltdown on Intel processor generations released as early as 2011. Currently, we have only verified Meltdown on Intel processors. At the moment, it is unclear whether AMD processors are also affected by Meltdown. According to ARM, some of their processors are also affected.
Which systems are affected by Spectre?
Almost every system is affected by Spectre: Desktops, Laptops, Cloud Servers, as well as Smartphones. More specifically, all modern processors capable of keeping many instructions in flight are potentially vulnerable. In particular, we have verified Spectre on Intel, AMD, and ARM processors.
Which cloud providers are affected by Meltdown?
Cloud providers which use Intel CPUs and Xen PV as virtualization without having patches applied.

Furthermore, cloud providers without real hardware virtualization, relying on containers that share one kernel, such as Docker, LXC, or OpenVZ are affected.What is the difference between Meltdown and Spectre?
Meltdown breaks the mechanism that keeps applications from accessing arbitrary system memory.
Consequently, applications can access system memory.
Spectre tricks other applications into accessing arbitrary locations in their memory.
Both attacks use side channels to obtain the information from the accessed memory location.
For a more technical discussion we refer to the papers ( Meltdown and Spectre)Why is it called Meltdown?
The vulnerability basically melts security boundaries which are normally enforced by the hardware.
Why is it called Spectre?
The name is based on the root cause, speculative execution. As it is not easy to fix, it will haunt us for quite some time.
Is there more technical information about Meltdown and Spectre?
Yes, there is an academic paper and a blog post about Meltdown, and an academic paper about Spectre.
 Furthermore, there is a Google Project Zero blog entry about both attacks.
Furthermore, there is a Google Project Zero blog entry about both attacks.What are CVE-2017-5753 and CVE-2017-5715?
CVE-2017-5753 and CVE-2017-5715 are the official references to Spectre. CVE is the Standard for Information Security Vulnerability Names maintained by MITRE.
What is the CVE-2017-5754?
CVE-2017-5754 is the official reference to Meltdown. CVE is the Standard for Information Security Vulnerability Names maintained by MITRE.
Can I see Meltdown in action?
Can I use the logo?
Both the Meltdown and Spectre logo are free to use, rights waived via CC0.
-xl.jpg) Logos are designed by Natascha Eibl.
Logos are designed by Natascha Eibl.Logo Logo with text Code illustration Meltdown PNG /
SVGPNG /
SVGPNG /
SVGSpectre PNG /
SVGPNG /
SVGPNG /
SVGIs there a proof-of-concept code?
Yes, there is a GitHub repository containing test code for Meltdown.
Where can I find official infos/security advisories of involved/affected companies?
Link Intel Security Advisory / Newsroom / Whitepaper ARM Security Update AMD Security Information RISC-V Blog NVIDIA Security Bulletin / Product Security Microsoft Security Guidance / Information regarding anti-virus software /
Azure Blog /
Windows (Client) / Windows (Server)Amazon Security Bulletin Google Project Zero Blog /
Need to knowAndroid Security Bulletin Apple Apple Support Lenovo Security Advisory IBM Blog Dell Knowledge Base / Knowledge Base (Server) Hewlett Packard Enterprise Vulnerability Alert HP Inc. 
Security Bulletin Huawei Security Notice Synology Security Advisory Cisco Security Advisory F5 Security Advisory Mozilla Security Blog Red Hat Vulnerability Response /
Performance ImpactsDebian Security Tracker Ubuntu Knowledge Base SUSE Vulnerability Response Fedora Kernel update Qubes Announcement Fortinet Advisory NetApp Advisory LLVM Spectre (Variant #2) Patch /
Review __builtin_load_no_speculate /
Review llvm. nospeculateload
nospeculateload
CERT Vulnerability Note MITRE CVE-2017-5715 / CVE-2017-5753 / CVE-2017-5754 VMWare Security Advisory / Blog Citrix Security Bulletin /
Security Bulletin (XenServer)Xen Security Advisory (XSA-254) / FAQ
Acknowledgements
We would like to thank Intel for awarding us with a bug bounty for the responsible disclosure process, and their professional handling of this issue through communicating a clear timeline and connecting all involved researchers.
Furthermore, we would also thank ARM for their fast response upon disclosing the issue.
This work was supported in part by the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation programme (grant agreement No 681402).
This work was supported in part by NSF awards #1514261 and #1652259, financial assistance award 70NANB15h428 from the U.S. Department of Commerce, National Institute of Standards and Technology, the 2017-2018 Rothschild Postdoctoral Fellowship, and the Defense Advanced Research Project Agency (DARPA) under Contract #FA8650-16-C-7622.
Fortinet Secure Processors
Secure Processing Units Overview
Fortinet continues to innovate and create new Secure Processing Units (SPUs) to fulfil one of our key founding principles: security devices should never become a performance bottleneck within a network and security architecture, nor should they sacrifice visibility, user experience, or security to achieve a required application performance. In short, to realize the promise of digital innovation.
Contact one of our Fortinet experts about our Secure Processing Units below.
Network Processor 7 (NP7)
Network Processors operate in-line to deliver unmatched performance for network functions and hyperscale for stateful firewall functions.
Read More About NP7
Content Processor 9 (CP9)
As a co-processor to the main CPU, Content Processors offload resource- intensive processing and drive content inspection to accelerate security functions.
Read More About CP9
System-on-a-Chip 4 (SoC4)
As a co-processor to the main CPU, Content Processors offload resource- intensive processing and drive content inspection to accelerate security functions.
Read More About SoC4
Networking Processing Unit: Engineered for Hyperscale
NP7 runs at the network layer to speed functions that typically slow CPUs, such as IPv4, IPv6, unicast, and multicast.
 In addition, NP7 accelerates IPsec decryption, VXLAN termination, and address translation, while providing hardware logging and policy enforcement.
In addition, NP7 accelerates IPsec decryption, VXLAN termination, and address translation, while providing hardware logging and policy enforcement.NP7 Key Benefits
Single-session flow with 100 Gbps throughput needed for high-bandwidth internet2 sites.
Millions of connections per second in hardware as required by high-demand e-commerce.
Single-digit microsecond latency as called for by a financial exchange.
NP7 Advantage
Specification FortiGate 1800F (NP7 ASIC) Security Compute Rating Firewall 198 Gbps 14x IPsec VPN 65 Gbps 15x Threat Protection 9.1 Gbps 2.5x SSL Inspection 17 Gbps 23x Concurrent Sessions 12M 4x Sessions per second 750k 7x Content Processing Unit: Engineered for Protection
The ninth generation of Fortinet Content Processor, CP9, is designed for protection.
 CP9 works as a CPU co-processor, taking on resource-intensive security functions such as Application Identification, IPS (pre-scan, signature correlation, etc.), and antivirus, so the CPU can perform other important tasks.
CP9 works as a CPU co-processor, taking on resource-intensive security functions such as Application Identification, IPS (pre-scan, signature correlation, etc.), and antivirus, so the CPU can perform other important tasks.CP9 also performs pattern matching acceleration, fast inspection of real-time traffic for application identification, all without compromising user experience.
CP 9 Key Benefits
Manages internal and external risks while reducing complexity
Protects applications while optimizing user experience
Removes blind spots without minimizing performance degradation
CP9 Advantage
Fortinet demonstrated high performance with minimal impact on SSL inspection in the 2019 NSS Labs Next-Generation Firewall Group Test Results.
System-on-a-Chip: Engineered for Efficiency
The fourth generation of the Fortinet System-on-a-Chip, SoC4, supports customer WAN edge transformation with the industry’s highest Security Compute Ratings.
 SoC4 consolidates both network and content processing functions on a single chip, delivering fast application identification, steering, and overlay performance.
SoC4 consolidates both network and content processing functions on a single chip, delivering fast application identification, steering, and overlay performance.SoC4 is a fully integrated set of security functions, including a Layer 7 firewall, on a fast and cost-effective chip. It meets the high-performance requirements for optimal end-user experience and secures branches deployed in SD-WAN environments.
SoC4 Key Benefits
Simplifies operations and automation
Delivers high-performance application experience with low TCO
SoC4 Advantage
Specification FortiGate 40F (SOC4 ASIC) Security Compute Rating Firewall 5 Gbps 9x IPsecVPN 4.4 Gbps 23x Threat protection 0.60 Gbps 3x SSL inspection 0.  31 Gbps
31 Gbps4x Concurrent sessions 700,000 5x Top 5 things to know about Microsoft’s Pluton Security Processor
Top 5 things to know about Microsoft’s Pluton Security Processor
Microsoft has a new security processor that’s getting some buzz. Tom Merritt explains.
Intel’s Trusted Platform Module has been good at improving security by creating a Secure Enclave for things like encryption keys, but it has had a few flaws. And now it has a successor: Microsoft’s Pluton Security Processor.

Listen to the podcast version of this Top 5 episode on SoundCloud
Here are five things to know about Microsoft’s Pluton Security Processor.
- Pluton won’t Meltdown or Spectre. It has built-in defenses against both side-channel attacks because it’s isolated from the rest of the system. It even has defenses to thwart future spin-offs of those kinds of attacks. The keys never leave the Pluton security boundary.
- Pluton is hard to attack physically, too. It’s integrated into the CPU die, so there’s nowhere for an attacker to solder leads into. There is no bus to attack.
- It has its roots in the Xbox. Microsoft developed an integrated security chip in cooperation with AMD back in 2013. They brought that over to Azure Sphere devices and in November 2020 announced Pluton for PCs.
- It plays nice with other security platforms. Pluton can provide a secure identity for the CPU itself, that complements security platforms including the Open Compute Project’s Project Cerberus, to enable root-of-trust and firmware authentication.
- It may be off in your laptop. Lenovo shipped its first ThinkPads with Pluton turned off. So, just because Pluton is in your CPU doesn’t mean it’s active. You may need to enable it yourself. Lenovo says they did this because enterprise customers wanted to test it before it was turned on for their workforce.
AMD and Qualcomm are making chips with Pluton in them, and Intel says it’s working on it. So, it should be easy to find a machine with Pluton if you want it.
Subscribe to TechRepublic Top 5 on YouTube for all the latest tech advice for business pros from Tom Merritt.
Tom Merritt
Published:
Modified:
See more Hardware
Also See
-
Learn ethical hacking for less than $50 with this online training
(TechRepublic Academy) -
LogRhythm vs SolarWinds | SIEM Tool Comparison
(TechRepublic) -
DevOps: A cheat sheet
(TechRepublic) -
Ethereum cheat sheet: Everything you need to know (free PDF)
(TechRepublic) -
Cloning tools: What they are and how to use them
(TechRepublic Premium) -
Tom Merritt’s Top 5 series
(TechRepublic on Flipboard)
Share: Top 5 things to know about Microsoft’s Pluton Security Processor
-
Hardware
-
Microsoft
Editor’s Picks
-
Image: Rawpixel/Adobe Stock
TechRepublic Premium
TechRepublic Premium editorial calendar: IT policies, checklists, toolkits, and research for download
TechRepublic Premium content helps you solve your toughest IT issues and jump-start your career or next project.
TechRepublic Staff
Published:
Modified:
Read MoreSee more TechRepublic Premium
-
Image: diy13/Adobe Stock
Software
Windows 11 22h3 is here
Windows 11 gets an annual update on September 20 plus monthly extra features. In enterprises, IT can choose when to roll those out.
Mary Branscombe
Published:
Modified:
Read MoreSee more Software
-
Image: Who is Danny/Adobe Stock
Edge
AI at the edge: 5 trends to watch
Edge AI offers opportunities for multiple applications.
 See what organizations are doing to incorporate it today and going forward.
See what organizations are doing to incorporate it today and going forward. Megan Crouse
Published:
Modified:
Read MoreSee more Edge
-
Image: Apple
Software
iPadOS cheat sheet: Everything you should know
This is a complete guide for Apple’s iPadOS. Find out more about iPadOS 16, supported devices, release dates and key features with our cheat sheet.
TechRepublic Staff
Published:
Modified:
Read MoreSee more Software
- Image: Worawut/Adobe Stock
-
Image: Bumblee_Dee, iStock/Getty Images
Software
108 Excel tips every user should master
Whether you are a Microsoft Excel beginner or an advanced user, you’ll benefit from these step-by-step tutorials.
TechRepublic Staff
Published:
Modified:
Read MoreSee more Software
Intel, AMD and Qualcomm processors will add Microsoft’s Pluton security chip instead of TPM. Right to repair under threat? / Habr
The other day it became known that three major chip manufacturers at once: Intel, AMD and Qualcomm, plan to embed a new Pluton security chip in their processors. It was developed jointly with Microsoft and will replace the current TPM module in the future. In any case, manufacturers told about such prospects.
As for Pluton, this chip is based on technologies that Microsoft has developed for the protection system of its Xbox One game console.
 The goal pursued by Microsoft was to prevent pirates from hacking the game console and preventing the launch of pirated games.
The goal pursued by Microsoft was to prevent pirates from hacking the game console and preventing the launch of pirated games. What kind of chip is this?
About him a day ago, Microsoft spoke in detail in his blog.
Today, the security of the operating system on most PCs depends on a chip called the Trusted Platform Module (TPM). It is a processor-independent element. It stores keys and OS integrity data. Windows has been working with TPM for more than 10 years, technologies such as Windows Hello and BitLocker directly depend on this chip.
Everything is fine, but attackers are finding more and more opportunities to successfully break TPM-based protection. Hacking technologies are becoming more and more complex, their goal is a communication channel between the processor and the chip. Usually, this is a bus that is vulnerable to spoofing or interception of data transmitted over it. Here the main problem is just the autonomy of the TPM chip and its remoteness from the central processor.
Pluton will radically change the situation in the direction of increased protection. Firstly, this chip will be integrated into the processor architecture, and secondly, it will be able to simulate TPM, completely replacing the Trusted Platform Module technology. By the way, TPM emulation makes it possible to keep current technologies compatible with each other, including all existing TPM specifications and APIs.
Microsoft’s blog says that Pluton will store personal data, encryption keys, user IDs, and so on. According to Microsoft representatives, it is impossible to somehow remove this data from the chip even if the attacker has physical access to the PC. Pluton has received a new Secure Hardware Cryptography Key (SHACK) technology, which makes it possible to make sure that the encryption keys have never been extracted from the chip.
As a result, entire classes of attack vectors are blocked. It is about repelling physical attacks while preventing the theft of credentials and encryption keys.
 It also provides the ability to control software and hardware. Pluton will also help maintain the integrity of the system, since there will be much less opportunity to change some components.
It also provides the ability to control software and hardware. Pluton will also help maintain the integrity of the system, since there will be much less opportunity to change some components. Where did Pluton come from?
According to company representatives, a similar protection system was used in the Xbox One, where it was tested for several years. The hardware developers for the console gradually improved the technology, so that in the end it «grew» from a purely console division.
Now Pluton is able to protect not only against known attacks, but also prevent attacks based on 0-day vulnerabilities. It is also compatible with Bitlocker encryption and Windows Hello authentication. Yes, so far the developers are only talking about the Windows OS — what will happen to other OSes installed on systems with a chip, Microsoft representatives have not yet explained.
How to update chip firmware?
The question is quite logical, because if this chip becomes part of the processor architecture, then how to update its firmware? As it turned out, everything is simple, the update will be done through the cloud — as far as you can understand, along with Windows updates.

This principle of updating makes it possible to always keep the firmware up to date, however, only if it is connected to the network, this is one and two, provided that the updates themselves are not blocked. Many PC users block Windows and app updates, wanting to take control of their PC and OS themselves.
When will the introduction of Pluton technology start?
It’s not clear yet. But the fact that it will start soon is absolutely certain. AMD, Qualcomm and other processor manufacturers have confirmed that they will integrate Pluton into their chip architectures. In the future, support for Linux will also appear, as the developers announced separately. True, when exactly, and how it will work, is also unclear. But Microsoft already uses some Linux-based products on its systems, where Pluton also works.
It turns out that everything is fine, computers will become super secure?
In general, the level of protection of the user’s personal data really needs to increase.
 In addition, the range of attack methods available to attackers will be narrowed. This is the positive side.
In addition, the range of attack methods available to attackers will be narrowed. This is the positive side. There is also a fly in the ointment in a barrel of honey. Thus, Pluton is ideally suited to protect DRM as well, elevating this technology to heights unattainable before. Since the processors will directly request updates from the servers, the hardware and software data can also be checked against a central database.
And if something is changed, individual PC functions can be blocked. Protection of licensed software and content is also moving to a new level. The same activation of Windows using specialized software will become impossible. Similarly, the computer will be able to check the license for the content being played.
True, David Weston, director of corporate OS security at Microsoft, said that Pluton was created solely to improve the security of user data, and not to protect digital content.
Some analogies
A similar story happened with Apple two years ago.
 Then the company added the T2 chip, embedding it in the latest models of branded laptops. True, it was not integrated with the central processor, but there were many problems associated with it.
Then the company added the T2 chip, embedding it in the latest models of branded laptops. True, it was not integrated with the central processor, but there were many problems associated with it. The good thing is that the chip does a really good job of protecting users’ personal data. In addition, it turned off the laptop’s microphone in hardware if the laptop’s lid was closed.
But the same chip blocked the possibility of repairing devices with it by unauthorized service centers and ordinary users. So the supporters of the “right to repair” once again found themselves in a difficult position.
As for the chip from Microsoft, it is not clear now whether the company will use such opportunities itself, will provide this opportunity to partners, or will do nothing. In general, one can imagine the moment when a laptop with an inauthentic RAM bar will declare the need to purchase RAM from the manufacturer. But now we can only guess about this, in order to learn more about all this, you will have to wait.
Fortinet Security Processors
Overview of security processors
Fortinet continues to innovate and create new security processors (SPUs) to implement one of our key principles: security appliances should never compromise network and security architecture performance, nor should they compromise visibility, quality of interaction with user or security to achieve the required application performance. In short, to realize the potential of digital innovation.
Contact one of the Fortinet experts below for information on our security processors.
Network Processor 7 (NP7)
Network processors are built into the network to provide unrivaled networking performance and hyperscale for the firewall’s connection statefulness.
More about NP7
Content Processor 9(CP9)
As an additional processor to the main processor, content processors offload resource-intensive processes and inspect content to speed up the implementation of security features.

Learn more about CP9
System on a Chip 4 (Soc4)
As an additional processor to the main processor, content processors offload resource-intensive processes and inspect content to speed up the implementation of security features.
Learn more about Soc4
Network Data Engine: Designed for Hyperscale
NP7 works at the network layer to speed up features that would normally slow down the CPU, such as Ipv4, Ipv6, unicast, and multicast. In addition, NP7 speeds up IPsec decryption, VXLAN termination, and address translation while maintaining hardware-level logging and policy enforcement.
Key Benefits of NP7
Single-session 100Gbps stream required for high speed internet2 sites.
Millions of connections per second at the hardware level to meet the requirements of high-demand e-commerce.
Delay in microseconds as required by financial transactions.
NP7 advantage
Feature Fortigate 1800F (NP7 ASIC) Security Compute Rating Firewall 198 Gbps 14x IPsec VPN 65 Gbps 15x Traffic protection 9.1 Gbps 2.5x SSL verification 17 Gbps 23x Parallel sessions 12 million 4 x Sessions per second 750 thousand 7 x Content Processor: Designed for protection
9th Generation Fortinet Content Processor, CP9, designed for protection.
 The CP9 works as a CPU co-processor, taking over resource-intensive security features such as SSL/TLS decryption (including TLS1.3), IPS, and antivirus so that the CPU can perform other critical tasks.
The CP9 works as a CPU co-processor, taking over resource-intensive security features such as SSL/TLS decryption (including TLS1.3), IPS, and antivirus so that the CPU can perform other critical tasks. CP9 also performs fast, real-time traffic inspection to identify applications without compromising the user experience. In addition, it provides full network visibility, thus eliminating blind spots.
Nine Key Benefits of SR
Manage internal and external risks and reduce complexity simultaneously
Protect the application and optimize the user experience
Eliminate blind spots without compromising performance
Advantage of CP9
Fortinet Demonstrates High Performance with Minimal Impact on SSL Inspection in NSS Labs 2019 Next Generation Firewall Group Test Results.
System on a Chip: Designed for Efficiency
The fourth generation of Fortinet System-on-a-Chip, Soc4 supports the WAN edge transformation of top-rated Security Compute Ratings customers.
 Soc4 combines networking and content processing functions in a single chip, enabling fast application identification, management, and layer performance.
Soc4 combines networking and content processing functions in a single chip, enabling fast application identification, management, and layer performance. Soc4 is a fully integrated set of security features, including Layer 7 firewall, in a fast and cost-effective chip. It meets high performance requirements for an optimal end-user experience and protects branch offices deployed in SD-WAN environments.
Key Benefits of Soc4
Simplify operations and automate
Enable high performance applications with low total cost of ownership
Benefits of Soc4
Feature FortiGate 40F (SOC4 ASIC) Security Compute Rating Firewall 5 Gbps 9 x IPsecVPN 4.4 Gbps 23x Traffic protection 0.  60 Gbps
60 Gbps 3 x SSL verification 0.31 Gbps 4 x Parallel sessions 700 000 5 x AMD and ARM processors are also affected by the memory security issue
3DNews Technologies and IT market. News comments on recent events AMD and ARM processors are also affected by…
The most interesting in the reviews
01/04/2018 [12:35],
Konstantin Khodakovsky
New details are coming in regarding an identified architectural problem with modern processors. Specialized resources tell that there are three main options for attacks related to memory security (1 — bounds check bypass CVE-2017-5753, 2 — branch target injection CVE-2017-5715 and 3 — rogue data cache load CVE-2017- 5754). They are given the conditional names Meltdown (“Catastrophe” — option 3 and 3a) and Specter (“Ghost” — options 1 and 2).
 We wrote about Meltdown — it makes it possible to overcome the barrier between applications and the internal memory of the operating system kernel, which allows you to access protected data from the OS memory.
We wrote about Meltdown — it makes it possible to overcome the barrier between applications and the internal memory of the operating system kernel, which allows you to access protected data from the OS memory. Specter, in turn, makes it possible to bypass a similar barrier, but between separate applications: in other words, one service can read information from the memory of another. Specter is noticeably more difficult to implement, but the fight against the vulnerability promises to be more difficult. The «ghost attack» will very likely become a longer-term problem that users and developers will have to deal with. That’s why the name was chosen.
Both attacks are described in detail on a separate site by security experts from Google Project Zero, Graz University of Technology and some other organizations. At the heart of the problems lies the method of speculative instruction execution — the instruction prediction technology used in modern processors and which allows accelerating the operation of chips.
 The processor, having free resources, can calculate some operations in advance and store the results in several levels of cache memory, and, if necessary, transfer them to the application. If the need does not arise, the data simply disappears. Here, with the help of various tricks with speculative execution, attackers can gain access to some important data stored in shared memory, and through them to the necessary applications.
The processor, having free resources, can calculate some operations in advance and store the results in several levels of cache memory, and, if necessary, transfer them to the application. If the need does not arise, the data simply disappears. Here, with the help of various tricks with speculative execution, attackers can gain access to some important data stored in shared memory, and through them to the necessary applications. Meltdown vulnerabilities affect all Intel processors that support out-of-order execution. These are almost all chips released since 1995, with the exception of the Itanium series in its entirety and Atom chips until 2013. There is currently no confirmation that ARM and AMD processors are affected by Meltdown.
But in the case of Specter, the situation is worse: it potentially affects most modern processors that can manage many instructions on the fly. Experts claim to have tested Specter on Intel, AMD and ARM processors. In other words, hundreds of millions of smartphones and tablets are being added to PCs and servers.
After some silence, Intel officially noted that the problem with memory security concerns not only its processors, adding that it is collaborating with AMD and ARM (not to mention various OS manufacturers) to develop an effective solution. The company also stressed that the impact on performance will be very dependent on the type of workload and should not be noticeable to the «average PC user». This is partly confirmed by early tests.
Intel also added that this is not a security hole, but rather software analysis methods that could potentially lead to the extraction of important data from devices. There is no possibility to damage, delete or modify data. However, if an attacker gets passwords through Meltdown or Specter attacks, then he will be able to inflict more sensitive damage. According to the head of Intel Brian Krzanich (Brian Krzanich), while there are no known cases of exploitation of the vulnerability by attackers. Intel and other companies are rumored to be releasing full details of the issue next week, along with the release of hotfixes and software patches.
The chip maker raised his voice, wanting only to comment on the reports. This is not surprising — if the problem really concerned only Intel chips, it would be a serious blow to the company’s credibility.
However, AMD rejects Intel’s claims that all modern processors are vulnerable, regardless of manufacturer, and claims that the risk to its chips is close to zero: “Hello. Speculation has now circulated regarding a potential security problem associated with modern microprocessors and speculative instruction execution. As always, when a potential security issue is identified AMD strives to provide the best possible protection for users and works with our entire ecosystem to evaluate and respond, if necessary, to speculative command execution-related attacks identified by the security team .
To be clear, the security research team identified three variants of speculative execution attacks. The level of threat and solutions of all three options differ depending on the microprocessor manufacturer, and AMD is not affected by all three attack options.
Due to the architecture differences between AMD and , we believe that there is almost zero risk for our processors at this time. We will provide more information later.»
ARM, whose chips are widely used in smartphones and other devices, has confirmed that some of its microprocessor architectures are susceptible to attacks, including high-performance Cortex-A cores (the set of vulnerabilities differs in the case of different chips). The Cortex-M series for wearables and the Internet of Things, for example, is free of the problem altogether. But Cortex-A15, A57, A72 and A75 can be subjected to all three types of attacks, including Meltdown. In the case of kernels modified by manufacturers like Apple A or Qualcomm Krait, separate studies should be carried out.
Google and Microsoft also spoke about their actions regarding the problem. The search giant, for example, said it has been taking action for a long time. In particular, Android devices with the latest security updates are not affected by the problem, and Google has not yet registered successful attacks.
Google Apps, App Engine, devices like the current Pixel and Nexus, Google Home, Chromecast, and Google Wi-Fi are also protected. Chrome 63 and Chrome OS 63 users can activate the «Site Isolation» test feature, which will become standard with the release of new versions on January 23 (not all Chromebooks, however, will receive patches — only current models).
Microsoft, meanwhile, released an extraordinary security update for Windows 10 on Wednesday and also issued an official statement: “We are aware of this issue that has affected the entire industry and are working closely with chip manufacturers to develop and test effective measures to protect our customers. . We are in the process of rolling out updates to cloud services and have also released updates to protect Windows clients from vulnerabilities affecting supported hardware chips from Intel, ARM, and AMD. We have not received information that would indicate the use of vulnerabilities to attack our customers.”
Update: RedHat reports exploits for similar vulnerabilities in other CPU architectures, including IBM System Z, POWER8 (Big Endian and Little Endian), and POWER9 (Little Endian).
AMD shared details about the vulnerability of its chips.
Sources:
If you notice an error, select it with the mouse and press CTRL+ENTER.
Related Content
Permanent URL: https://3dnews.ru/963653
Headings:
Hardware news, processors, comments on recent events,Tags:
intel, amd, arm, google, microsoft, processor, security, vulnerabilities←
past
To the future →Holes in the processor. More than a billion computers are vulnerable to hackers — Moscow 24, 01/11/2018
Economics
January 11, 2018, 00:06
economics technology security
2018 began with a global shock for the global computer community: on January 2, the professional online magazine The Register published an article that a vulnerability was discovered in Intel processors, which allows hackers to access any information.
Not only personal computers and laptops, but also mobile devices, as well as servers of «cloud» information storages, were at risk.
Photo: depositphotos/DragonImages
Intel confirmed this information, stressing that the vulnerability became known in mid-December, about which the company warned its business partners. As it turned out, the company planned to release an official statement about the problem after measures were developed to close the hole.
However, few people were reassured by this statement by Intel, since the discovered vulnerability, firstly, has existed for more than 20 years, and secondly, similar problems were found not only in Intel processors, but also in products from other manufacturers — AMD and ARM Holdings. In general, we are talking about about a billion devices, which led some analysts to call the discovered vulnerability the most serious security hole in the history of computers.
In fact, we are talking about not one, but two holes, named accordingly — Meltdown, which allows a hacker to penetrate the processor’s memory, and Specter, which allows to interfere with running processes.
Both vulnerabilities open up opportunities for access to processor core memory using a new type of hacker attack based on the analysis of command execution time (timing attack).
How it works
The processor core memory is divided into two areas, the kernel address space and the user address space. These areas are separated at the processor protection level, and if you try to access the memory of the same address space, the processor will report an error.
But there is one important point. The clock frequency of processors in recent decades has grown much faster than the speed of RAM, so the processors have their own RAM — the so-called caches of the 1st, 2nd and 3rd levels, which also made it possible to increase the speed of computers, because if Since more than 100 processor cycles are needed for RAM, information can be retrieved from the L1 cache in a couple of cycles.
The Meltdown vulnerability could allow hackers to gain access to information such as passwords and computer encryption keys that can be used to access encrypted messages.
The Meltdown vulnerability allows analyzing the speed of calculations in the processor core and, based on this, calculating the data contained in the cache in the user’s address space. According to Intel, Meltdown allows hackers to gain access to information such as passwords and computer encryption keys that can be used to access encrypted messages.
The Specter vulnerability is related to a branch predictor function in the processor: if the program code contains an if statement, the processor determines the likelihood that it will have to access a particular memory area. This opens up the possibility of directing it to a cell with an instruction embedded by a hacker. In other words, this hole allows you to deceive a computer program and thereby gain access to confidential data.
Photo: TASS/Sergey Konkov
Dangerous protection
The most annoying thing about new vulnerabilities is that hacker attacks using them cannot be detected. It is also difficult to prevent, since they are not related to software, but to the internal architecture of processors, that is, to eliminate holes, a deep reworking of the processor architecture is required with a change in the location of transistors on the chip and calculation schemes.
Experts are sure that neither Intel nor other processor manufacturers are ready for this yet.
Now the emphasis is on software. So, on January 4, Microsoft released a security update for Windows operating systems that fixes the Meltdown vulnerability. However, the cure turned out to be worse than the disease itself.
At first, users began to complain that after the update, the computers began to slow down and overheat. Complaints statistics showed that the decrease in processor performance can reach 30%, the need for a heat sink increases by 10-15%, the computer’s power consumption increases by 10-30%, and, in addition, performance with read / write operations is significantly reduced. Intel representatives called these estimates exaggerated, noting that the performance of the computer depends on the workload and the impact of updates on the devices of ordinary users «should not be significant.»
After downloading an update, the Start menu and taskbar do not open on devices, and downloading updates on Windows 10, Windows 8.
1, and Windows 7 resulted in a system error on computers known as the blue screen of death.
However, things got even worse: some computers stopped booting altogether after installing updates. Microsoft acknowledged that after downloading the update, the Start menu and taskbar do not open on devices, and downloading updates on Windows 10, Windows 8.1 and Windows 7 led to a system error on computers, known as the blue screen of death.
At the same time, Microsoft representatives stated that such a problem occurs only on computers equipped with AMD processors, and accused processor manufacturers of hiding the real technical characteristics of their products. AMD, in turn, said that together with Microsoft is working on a speedy solution to the problem.
Rubchenko Maxim
Intel, AMD and Qualcomm processors will incorporate a Microsoft security chip from the Xbox 9 game console0001
Security
Technical protection
Technology|
Share
Intel, AMD and Qualcomm plan to integrate the Pluton security chip developed jointly with Microsoft into their future processors.
The novelty should come to replace the TPM module located separately from the processor and is designed to protect computers running Windows, including from attacks that require physical access to the machine. Pluton is based on technologies that Microsoft applied in the development of the anti-piracy system for its own Xbox One game console.
Microsoft security chip
Microsoft has partnered with AMD, Intel and Qualcomm to develop a security processor designed to protect computers running the Windows operating system. This was reported to CNews in the press service of the company. It is expected that the novelty called Pluton will eventually replace the current Trusted Platform Modules (TPM, Trusted Platform Module).
Unlike TPM chips, Microsoft’s hardware solution is integrated directly into the CPU instead of being separately located on the motherboard. Pluton is designed to provide more powerful hardware and software integration on Windows PCs, eliminating entire classes of attack vectors, Microsoft explains.
The use of Pluton, as noted by Microsoft, will improve the ability to repel physical attacks, prevent theft of credentials and encryption keys, as well as provide the ability to control hardware and software and check the integrity of the system. The firmware of the microcircuit will be updated using the cloud, in much the same way as Windows 10 does now — through the Windows Update service.
Pluton’s security technologies were previously applied to the hardware and OS security of Microsoft’s Xbox One game console, which was built in partnership with AMD.
The new security chip will be integrated into the next generation of processors from Microsoft partners AMD, Intel and Qualcomm, the largest manufacturers of Windows PC processors. Microsoft did not specify whether Pluton will become a mandatory component of future central processing units, and when exactly such chips will appear on the market.
Replacement for TPM
Today, the security kernel of an OS is typically located on a chip separate from the CPU called a Trusted Platform Module (TPM).
TPM is used to securely store keys and evaluation parameters that verify the integrity of the system. TPMs have been in Windows for over 10 years and support technologies such as Windows Hello (biometric authentication) and Bitlocker (media encryption).
Since the TPM and the CPU are physically separated from each other, the link in the system becomes a communication channel between these devices, which is usually a bus interface. That is, if there is physical access to a computer with TPM, an attacker can steal or replace the transmitted information. Pluton, according to Microsoft, solves this problem.
Windows and Pluton computers will initially emulate TPM, allowing for a smooth transition from TPM to Pluton that is seamless and transparent to the end user. The Microsoft Security Processor will be used to protect credentials, user IDs, encryption keys, and personal data. None of this information can be removed from Pluton, even if an attacker installs malware or takes full physical control of the computer, Microsoft says.
Microsoft Pluton integrates directly into the
CPU
The technologies featured in Pluton were first implemented as part of integrated hardware and OS security in the Xbox One console released in 2013 by Microsoft in partnership with AMD and the Azure Sphere IoT platform.
Ruslan Rakhmetov, Security Vision: Russian business is interested in offers from MSSP providers
Safety
According to The Verge, physically attacking a Pluton-equipped PC with Windows on board would be as difficult as making an Xbox One console run pirated games. And if it is possible, it is extremely difficult.
Safety reverse side
According to The Verge, the appearance of Pluton can cause dissatisfaction with opponents of DRM (Digital Rights Management) technical means of protecting copyright and related rights, which are widely used around the world to restrict the copying or modification of digital content (video, audio game programs).
According to David Weston , director of corporate security and OS security at Microsoft, the new technology can indeed be used to protect digital content, but Pluton was not created for this, but to increase security.
The fact that new chips are tied to the Microsoft cloud can also cause concern. The corporation, in fact, gets exclusive access to one of the most important components of the computer. Thus, the stability and safety of the machine will depend on the quality of the released firmware updates.
- The best Russian video communication software: looking for a replacement for Teams and Zoom
Dmitry Stepanov
Elbrus creators declared Intel and AMD processors a threat to Russia’s national security
Business
Legislation
IT in the public sector
Technique|
Share
The manufacturer of Elbrus called the admission of computer equipment for foreign processors to public procurement «a direct threat to Russia’s national security.
» This is how the MCST company reacted to the project of the Ministry of Industry and Trade, which opens up access to tenders for equipment on foreign CPUs. The creators of Baikal processors, on the contrary, see numerous advantages for the market in the idea of the Ministry of Industry and Trade.
Foreign processors threaten Russia
The developer of domestic Elbrus processors, the MCST company, saw a threat to Russia’s national security in a project to admit foreign processors to public procurement. According to RBC, this idea of the authorities was personally criticized by the general director of the company Alexander Kim .
Kim expressed his opinion in a letter sent at the end of 2021 to several government departments at once. The list of recipients includes the Ministry of Digital Development, the Ministry of Finance, the Ministry of Economic Development and the Federal Antimonopoly Service (FAS).
Alexander Kim, argues that the draft amendments to Government Decree No. 719 “On Confirming the Production of Industrial Products on the Territory of Russia” are contrary to the doctrine of information security, which the President of Russia Vladimir Putin approved in the summer of 2021. According to him, the document also contradicts Russian strategy for the development of the electronics industry until 2030
MCST sees a huge danger for Russia in foreign processors, including American
Representatives of the Ministry of Digital Development confirmed to CNews that they had received the letter.
More about project
The project, criticized by the head of the MCST, is the brainchild of the Russian Ministry of Industry and Trade. It describes a scoring system for evaluating equipment for inclusion in the register of Russian radio-electronic products. The document also considers a delay on the mandatory use of domestic processors until 2024.
Alexander Kim emphasized that the new rules dictated by the project make it possible to score enough points to enter devices into the registry even if there is no Russian processor in it and the mandatory installation of motherboards containing these processors in Russia. The CEO of the MCST emphasized that manufacturers can easily circumvent the restrictions by scoring the required amount of points through the use of less significant domestic-made electronic modules.
As CNews reported, the current rules state that in order to enter the registry, storage systems must be built on Russian CPUs from January 1, 2021. This rule applies to laptops, tablets, PDAs and electronic notebooks weighing no more than 10 kg from July 1 2021, and for computers, copy and print devices, motherboards and solid state drives from January 1, 2022
Entry of equipment into the register allows manufacturers to sell it to Critical Information Infrastructure (CII) entities. These include government organizations, legal entities and individual entrepreneurs who own information systems from a number of strategically important industries: transport, telecommunications, banking, nuclear energy, fuel and energy complex, healthcare, science, metallurgy, defense, rocket and space and chemical industries.
Consequences on an unprecedented scale
The loophole in the project of the Ministry of Industry and Trade discovered by the head of the Elbrus developer will have a sharp negative impact on interest in domestic CPUs. According to Alexander Kim, the demand for them will quickly fall.
Kim believes that this can lead to stagnation of products in warehouses. According to his calculations, the new rules could make over $20 million worth of processors and components unclaimed.
“Weakening of requirements will facilitate the entry of localized products of foreign manufacturers into the register <...>. The penetration of foreign platforms into the critical information infrastructure <...> will continue, which will lead to a deterioration in the information security of the digital economy as a whole. This is a direct threat to the national security of Russia,” said Alexander Kim in his letter.
According to an unnamed representative of the MCST, who confirmed to RBC that the letter was sent, if PCs based on foreign processors start to get into the register of Russian radio-electronic products, this will affect the security of the CII.
He emphasized that both CII and government agencies «will, as now, be available for cyber attacks, without prospects for improving the situation.»
How to solve the problem
In his letter, Alexander Kim suggested a way to solve the problem, which, in his opinion, is the project of the Ministry of Industry and Trade. It consists in maintaining Government Decree No. 719without any changes.
Kim also suggested creating a separate segment in the registry, which would include Russian equipment based on foreign processors, and calling it «Localized Products». He proposed to give this kind of equipment all the preferences at the auction on the principle of «second extra», but to deprive it of access to all tenders organized by CII subjects.
Commentary of the Ministry of Industry and Trade
The project of the Ministry of Industry and Trade was published on December 30, 2021. Among other things, it proposes the idea of implementing a two-level system for admitting computer equipment to Russian public procurement.
Drones, robots and VR: what innovations are in demand in metallurgy
Industry innovation
First level appliances are devices based on a Russian processor. The second level is assigned to equipment without such a CPU, but at the same time listed in the register of Russian electronics. According to the idea of the ministry, if there is an application for the supply of equipment on Russian chips in the tender, the applications of equipment manufacturers for foreign CPUs should be rejected.
As representatives of the Ministry of Industry and Trade told RBC, the draft government decree is currently at the stage of interdepartmental coordination. “A prerequisite for computer technology will be the use of a Russian central processor or confirmation of costs for the purchase of such processors, its development or production. The manufacturer will receive the maximum number of points when using the Russian processor in its products, the “passing” score for obtaining the status will increase annually and over time it will be impossible to get it without using the Russian processor, ”they said to the publication.
Commentary of the Ministry of Digital
Representatives of the Ministry of Digital Development believe that it is important «to maintain a balance between meeting the needs of the market and the development of Russian microelectronics.» “Russian manufacturers of microelectronics need not worry about losing their customers: high-quality products will always be in demand among consumers. Priority will always be given to Russian manufacturers,” representatives of the ministry told CNews.
According to them, “the security of CII subjects is one of the goals of the development of the Russian digital economy. This issue is now being dealt with by several departments, including the Ministry of Digital Development. When making decisions, risks, opportunities are taken into account and various scenarios are evaluated.
Anton Smirnov, AI Cloud: AI magic begins where servers are combined into “teams”
Artificial intelligence
“We have repeatedly discussed with representatives of the MCST and other representatives of manufacturers of regulatory options.
We support the initiatives of the Ministry of Industry and Trade, they have been developed in close contact with the experts of the Ministry of Digital Development,” added representatives of the Ministry of Digital Development.
Opinions «for»
Baikal Electronics, a developer of domestic Baikal processors, does not share Alexander Kim’s opinion regarding the threat to national security in the project of the Ministry of Industry and Trade. As the development director of Baikal Electronics told RBC Vitaly Bogdanov , the ministry’s idea for a new scoring system «benefits both processor developers and Russian hardware manufacturers.»
According to Bogdanov, “from 2024, the system will not allow equipment without a domestic processor to be included in the register.” He also added that «the regulator and Russian developers have yet to work on mechanisms for monitoring compliance with the requirements.»
In support of amendments to Government Decree No.
719the director for interaction with state and public organizations of the KNS-group (produces servers under the Yadro brand) Natalia Grigoryeva is speaking. She is sure that the current version of the document «leaves ample opportunities to manipulate the cost of the constituent elements of the final product in order to achieve the necessary indicators in order to recognize the products as domestic.» She also added that «the recognition of domestic products exclusively on Russian processors will cause irreparable damage to the entire industry.»
Numerous ideas of the Ministry of Industry and Trade
Starting from mid-2021, the Ministry of Industry and Trade has issued several draft government regulations (they partly contradict each other, and none has yet been adopted), which radically change the rules of the game for the Russian radio-electronic industry, previously consistently established by the state for several years.
In particular, the ministry proposed assigning scores to electronic products from the “computer technology” category (code 26.
