IEEE SA — Registration Authority
IEEE offers Registration Authority programs or registries which maintain lists of unique identifiers under standards and issue unique identifiers to those wishing to register them. The IEEE Registration Authority assigns unambiguous names to objects in a way which makes the assignment available to interested parties.
View in: Chinese | English | Japanese | Korean | Russian
View Infographic
Public Listing
Download Public Listing
- IEEE MA-L Assignments (CSV)
- IEEE MA-M Assignments (CSV)
- IEEE MA-S Assignments (CSV)
- IEEE IAB Assignments (CSV)
- IEEE CID Assignments (CSV)
- IEEE EtherType™ Assignments (CSV)
- IEEE Manufacturer ID Assignments (CSV)
- IEEE Operator ID Assignments (CSV)
- IEEE PSID Assignment
- IEEE Logical Link Control Assignments
- IEEE Standards Group Assignments
- IEEE STID Assignments
Registries
MAC Address Block Large (MA-L)
An MA-L assignment includes an OUI and large blocks of EUI-48 and EUI-64 values which can be used as MAC Addresses, Bluetooth Device Addresses, Ethernet Addresses or object identifiers.
Learn More
MAC Address Block Medium (MA-M)
An MA-M assignment includes medium blocks of EUI-48 and EUI-64 values which can be used as MAC Addresses, Bluetooth Device Addresses, Ethernet Addresses or object identifiers.
Learn More
MAC Address Block Small (MA-S)
An MA-S assignment includes an OUI-36 and small blocks of EUI-48 and EUI-64 values which can be used as MAC Addresses, Bluetooth Device Addresses, Ethernet Addresses or object identifiers.
Learn More
Company ID (CID)
A unique 24-bit identifier that cannot be used to generate EUI-48 or EUI-64 values. Therefore, the CID is especially applicable in applications where unique MAC addresses are not required.
Learn More
EtherType™
Provides a context for interpretation of the data field of an Ethernet/IEEE 802.3 data frame (protocol identification).
Learn More
Manufacturer ID
The manufacturer of a transducer is defined with a 14-bit code called the manufacturer ID.
Learn More
Logical Link Control (LLC)
Contains addressing information that consists of the Destination Service Access Point (DSAP) and the Source Service Access Point (SSAP) address field.
Learn More
AcpcTreeId
An identifier for a specific set of binary trees used to convey certificate access codes to certificate users who are using the Activation Codes for Pseudonym Certificates (ACPC) technique specified in IEEE Std 1609.2.1. The assignee of an AcpcTreeId is assigned to operate an ACPC Certificate Access Manager using that AcpcTreeId.
Learn More
Unique Registration Number (URN)
A 64-bit unique identifier contained in memory devices, or nodes, in which IEEE 1451.4 TEDS data is stored.
Learn More
IEEE Template/TDL Item
IEEE template is a definition of the placement and significance of each piece of data stored within the TEDS memory. A TDL’s purpose is to map bits.
Learn More
Provider Service Identifier (PSID)
Used by IEEE 1609 standards to identify a particular application service provider that announces it is providing a service to potential users of an application or service.
Learn More
IEEE 802.16 Operator ID
A 24-bit number that is broadcast by a base station as part of its Base Station ID.
Learn More
Standard Group MAC Address
NOTE: For Standards Development use ONLY. A Universally Administered Address Block allocated for the assignment of Group MAC Addresses for use in Standards.
Learn More
IEEE 1667 Silo Type Identifier (STID)
IEEE 1667 specifies the interface to and behavior of several silos (e.g., Probe Silo, TCG Storage Transport Silo, Password Silo, and Smart Card Transport Silo). External silos may be defined outside of the standard, be either public or private, and involve third-party licensing. Guidelines for external silos are specified in IEEE 1667.
Learn More
IEEE Std 1588™ sdoId
The sdoId (Standards Development Organization Identifier) is a protocol attribute, per IEEE Std 1588, that identifies the PTP Profile in use by the PTP Instance.
Learn More
ElectorGroupId
An identifier for a Certificate Trust List series allowing for the management of roots of trust within the certificate management system as specified in IEEE Std 1609. 2.1. The assignee of an ElectorGroupId serves as the SCMS Manager of that ElectorGroupId.
2.1. The assignee of an ElectorGroupId serves as the SCMS Manager of that ElectorGroupId.
Learn More
Registration Authority Governance and Additional Information
The IEEE Registration Authority operates under the direction of the IEEE SA Board of Governors.
Registration Authority Committee (RAC)
Oversight committee that assists standard developing organizations to establish unambiguous, sustainable registration authorities.
Learn More
Tutorials
Informative documents to assist with learning more about IEEE Standard Association Registries.
Learn More
Credit Application Form
For those interested in paying for a registry via purchase order.
Learn More
FAQs
The commonly most asked questions about our registries and how they are used.
Learn More
Contact Us
Contact Registration Authority staff via [email protected], snail mail, phone or fax.
Learn More
mac address — IEEE Registration Authority mac prefix
Asked
Modified
3 years, 4 months ago
Viewed
3k times
I’m analyzing a big list of devices, and trying to detect the type of each one of them using different data. one of the data types I have is MAC Address, and i encountered the following mac address prefix — 40:ed:98.
one of the data types I have is MAC Address, and i encountered the following mac address prefix — 40:ed:98.
Searching some sites it says that the mac address belong to IEEE Registration Authority, the authority that sets the mac prefixes to different companies.
As far as i know and looked — IEEE doesn’t make devices — so which company does the prefix actually belong to ?
Thanks
- mac-address
The main problem is that those websites have an outdated concept of how OUIs work. Manufacturer prefixes are not always 24 bits long – they used to be in the past, but now IEEE offers both 28-bit and 36-bit prefixes (for a reduced price).
So when you see a 24-bit prefix that is allocated to IEEE itself, that means it’s the «base» from which IEEE assigns those longer prefixes. For example, 40-ED-98-3 is assigned to Knox and 40-ED-98-7 is assigned to Vaisala Oyj.
You’ll find the real assignments beginning with 40-ED-98 in the OUI-28 (MA-M) registry. There are three vendor prefix registries:
There are three vendor prefix registries:
- MA-L: http://standards-oui.ieee.org/oui/oui.txt
- MA-M: http://standards-oui.ieee.org/oui28/mam.txt
- MA-S: http://standards-oui.ieee.org/oui36/oui36.txt
with a web-based search page here (select «All MAC (MA-L, MA-M, MA-S)» as the database).
(It’s a very similar situation as with IPv4 «classful» addresses – everyone used to get the same size block, and it turned out that there are not enough possible ‘prefixes’, and at the same time many manufacturers really need a much smaller block than is offered. So the solution was to designate a block of longer prefixes.)
Some MAC addresses from the Wireshark database
40:ED:98:00:00:00/28 Tsinghua Tsinghua Tongfang Co., LTD 40:ED:98:10:00:00/28 Guangzho GuangZhou FiiO Electronics Technology Co.,Ltd 40:ED:98:20:00:00/28 A-Iox A-Iox Inc. 40:ED:98:30:00:00/28 Knox Knox Company 40:ED:98:40:00:00/28 Kendrion Kendrion Kuhnke Automation GmbH 40:ED:98:50:00:00/28 Cape 40:ED:98:60:00:00/28 Shanghai Shanghai Broadwan Communications Co.,Ltd 40:ED:98:70:00:00/28 VaisalaO Vaisala Oyj 40:ED:98:80:00:00/28 Guangzho Guangzhou Auric Intelligent Technology Co.,Ltd. 40:ED:98:90:00:00/28 Teratron TeraTron GmbH 40:ED:98:A0:00:00/28 Integrat Integrated Design Ltd 40:ED:98:B0:00:00/28 SiebertI Siebert Industrieelektronik GmbH 40:ED:98:C0:00:00/28 Bloomsky BloomSky,Inc. 40:ED:98:D0:00:00/28 Hangzhou Hangzhou GANX Technology Co.,Ltd. 40:ED:98:E0:00:00/28 BordaTec Borda Technology
That is a prefix for a 20-bit sub-block allocated by IEEE. You need to look at the next nybble for company ID in the MAC Address Block Medium (MA-M) list.
Sign up or log in
Sign up using Google
Sign up using Facebook
Sign up using Email and Password
Post as a guest
Required, but never shown
Post as a guest
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
ZigBee networks.
 Why and why? / Habr
Why and why? / Habr
Why are you scratching your turnip?
You need a different net for a goldfish!
Actually, I was going to continue a series of topics on the work of RTLS — real-time positioning system. Namely, to talk about the wireless infrastructure of the system based on ZigBee networks. But suddenly I was surprised to find that there are no publications on Habrahabr devoted to the IEEE 802.15.4 standard and the ZigBee specification. There are only a few references associated with a particular application. I will try my best to fill this gap. nine0008
Recently, wireless sensor networks are gaining more and more importance. Networks that, by their purpose, parameters, specifications, differ significantly from communication networks — WiFi, GSM, LTE, etc. Among others used in sensor networks, the ZigBee specification stands out — the most advanced add-on to the IEEE 802.15.4
standard.
This year marks 10 years since the founding of the ZigBee Alliance, and in October it will be 5 years since the current ZigBee Pro Feature Set 2006 specification was approved. So the publication can be considered an anniversary. nine0008
So the publication can be considered an anniversary. nine0008
Those wishing to get acquainted with a self-organizing self-healing sensor network that does not require special frequency resolution, please under cat.
I’ll start with the questions in the title:
Why?
Many applications require wireless networks that are not high speed but are reliable, robust (self-healing), easy to deploy and easy to operate. It is also important that the equipment of such networks allows long-term operation from autonomous power sources, has a low cost, and is compact. An example of such an application is «smart home». nine0005
Until 10 years ago, none of the network standards met this combination of requirements, which led to the creation of the IEEE 802.15.4 and ZigBee standards, which describe stable, scalable, multihop wireless networks that are easy to deploy and support a variety of applications.
Why ZigBee?
ZigBee networks, unlike other wireless data networks, fully satisfy the requirements listed above, namely:
a) thanks to the mesh topology of the network and the use of special routing algorithms, the ZigBee network provides self-healing and guaranteed delivery of packets in cases of a break in communication between individual nodes (obstacles), overload or failure of some element; nine0005
b) the ZigBee specification provides for cryptographic protection of data transmitted over wireless channels and a flexible security policy;
c) ZigBee devices are characterized by low power consumption, especially end devices for which a “sleep” mode is provided, which allows these devices to work up to three years from one ordinary AA and even AAA battery;
d) ZigBee network is self-organizing, its structure is set by the parameters of the configurator stack profile and is formed automatically by attaching (re-attaching) devices forming it to the network, which ensures ease of deployment and ease of scaling by simply attaching additional devices; nine0005
e) ZigBee devices are compact and relatively inexpensive.
Communication in the ZigBee network is carried out by sequential relaying of packets from the source node to the destination node. The ZigBee network provides several alternative routing algorithms, the selection of which occurs automatically.
The standard provides for the possibility of using channels in several frequency ranges. The highest transmission speed and the best noise immunity are achieved in the range from 2.4 to 2.48 GHz. This range has 16 channels of 5 MHz. nine0005
The price that had to be paid in ZigBee networks for minimizing power consumption, compactness and low cost is a relatively low data transfer rate.
«Gross» speed (including service information) is 250 kbps. The average payload data transfer rate, depending on the network load and the number of retransmissions, ranges from 5 to 40 kbps.
The distance between network workstations is tens of meters indoors and hundreds of meters outdoors. Due to relaying, the area covered by the network can be very significant: up to several thousand square meters indoors and up to several hectares in open space.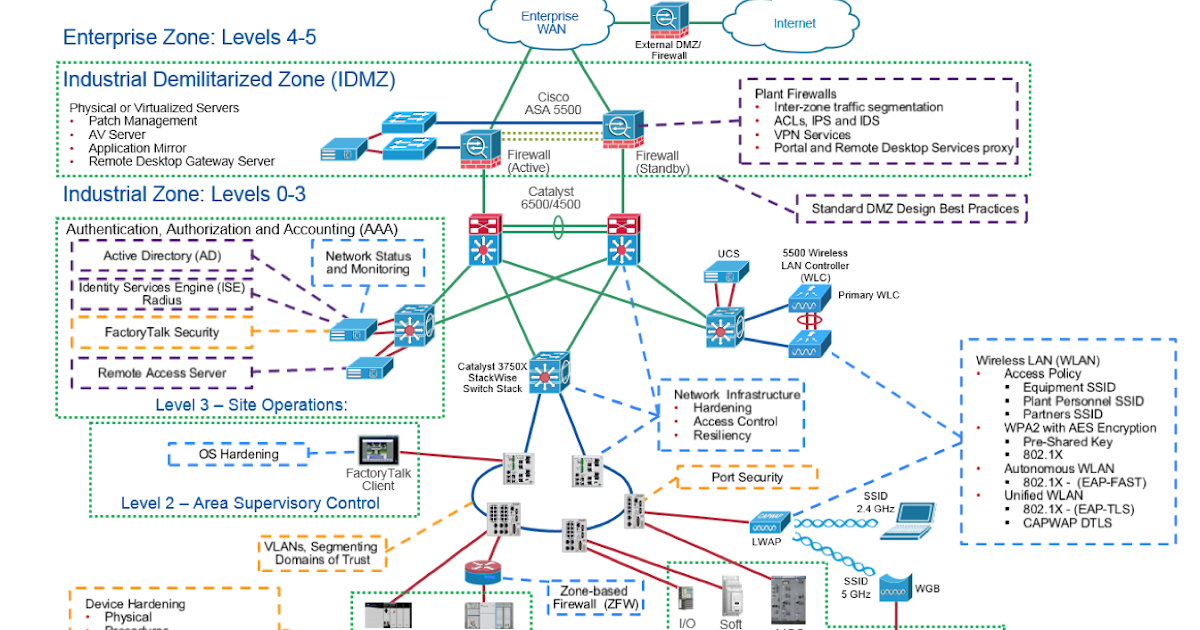 Moreover, the ZigBee network can be expanded at any time by adding new elements or, on the contrary, divided into several zones by simply assigning an appropriate number of new network configurators. This can be useful for reducing the load and, accordingly, increasing the data transfer rate. nine0008
Moreover, the ZigBee network can be expanded at any time by adding new elements or, on the contrary, divided into several zones by simply assigning an appropriate number of new network configurators. This can be useful for reducing the load and, accordingly, increasing the data transfer rate. nine0008
A bit of history
The ZigBee Alliance was founded in 2002. Now it includes more than 300 companies. The goal of the alliance is to develop efficient wireless network protocols and ensure interoperability between devices from different manufacturers. The first standards were «born» in 2003 and were actively improved and expanded.
Stochastic addressing, Many-to-One and Source Routing mechanisms, as well as the ability to detect asymmetric links were introduced, which increased the efficiency of ZigBee networks for a number of specific applications. nine0005
Standard application profiles and a library of standard clusters have been developed. This significantly simplified the development of applications, facilitated and accelerated the implementation of new solutions using equipment from different manufacturers.
This significantly simplified the development of applications, facilitated and accelerated the implementation of new solutions using equipment from different manufacturers.
A number of new mechanisms have been introduced to increase the security and reliability of the network.
An automatic transition to a «clean» frequency channel is provided in case of interference.
The current ZigBee Pro Feature Set 2006 specification was adopted in October 2007.
ZigBee devices
ZigBee networks are built from base stations of three main types: coordinators, routers, and end devices.
Coordinator starts and manages the network. It forms a network, performs the functions of a network control center and a trust center (trust center) — sets a security policy, sets settings in the process of connecting devices to a network, and manages security keys.
Router broadcasts packets, performs dynamic routing, restores routes in case of network congestion or failure of any device. When forming a network, routers are attached to the coordinator or other routers, and may be connected to child devices — routers and end devices. Routers operate continuously, have stationary power and can serve “sleeping” devices. The router can serve up to 32 sleeping devices. nine0005 End device can receive and send packets, but does not translate and route them. End devices can connect to a coordinator or router, but cannot have child devices.
When forming a network, routers are attached to the coordinator or other routers, and may be connected to child devices — routers and end devices. Routers operate continuously, have stationary power and can serve “sleeping” devices. The router can serve up to 32 sleeping devices. nine0005 End device can receive and send packets, but does not translate and route them. End devices can connect to a coordinator or router, but cannot have child devices.
End devices can be put into sleep mode to conserve battery power. It is the end devices that deal with sensors, local controllers and actuators.
Networking
The ZigBee network is self-organizing, and its work begins with the formation. Designated as a Personal Area Network Coordinator (PAN Coordinator) at design time, the device determines an interference-free channel and waits for connection requests.
Devices attempting to join the network send out a broadcast request. As long as the PAN coordinator is the only device on the network, it is the only one that answers the request and grants connection to the network. In the future, joining the network can also be provided by routers that have joined the network. nine0005
As long as the PAN coordinator is the only device on the network, it is the only one that answers the request and grants connection to the network. In the future, joining the network can also be provided by routers that have joined the network. nine0005
The device that received the response to the broadcast request exchanges messages with the joining device to determine whether to join. Capability is determined by the ability of the joining router to serve new devices in addition to previously connected ones.
Joining the network (connection)
There are two ways to join: MAC association and network rejoin (NWK rejoin).
MAC Association
MAC association is available to any ZigBee device and takes place at the MAC level. The MAC association mechanism is as follows:
A device that allows you to join it sets permission to join at the MAC level.
A device joining the network issues a MAC layer join request and broadcasts a beacon request.
Having received a beacon from devices that are ready to connect, the connecting device determines which network and which device it wants to join, and sets a MAC-level entry request with the «re-join» flag set to FALSE. nine0005
The joining device then sends a join request to the device selected to join and receives a response with the network address assigned to it.
With MAC association, the data is transmitted unencrypted, so the MAC association is not secure.
Re-network connection Re-network connection, contrary to the name, can also be used for the initial connection. It is performed at the network layer. However, if the incoming device knows the current network key, the packet exchange can be secure. The key can be obtained, for example, during setup. nine0005
When reconnecting, the joining device submits a join request at the network level and exchanges “join request” – “join request response” packets with the connecting device.
Network dynamics
In addition to new devices joining, the network structure also changes when devices leave the network and rejoin elsewhere (this happens, for example, when a device is rebooted).
The figure below is an example of reconnection. Device with address «0E3B» reconnects as «097D» and then as «0260». Each time it joins a different router, it obtains an address from the range of addresses available to the joining router.
End device reconnection in a tree network
Network protocols
The protocols regulated by the IEEE 802.15.4 and ZigBee 2007 Specification standards ensure the formation and operation of a wireless sensor network.
The IEEE 802.15.4 standard defines the physical and MAC layers, while the ZigBee specification defines the network layer and the application layer. The figure shows the ZigBee protocol stack. nine0008
ZigBee protocol stack
Excuse me, but at this point I have to interrupt due to late time. A description of the protocol stack can be found here: http://www.rtlsnet.ru/technology/view/3.
If the Habravchans show interest in the topic, I undertake to describe the stack profile, network topology options, routing algorithms, application profiles, clusters, endpoints, bindings, and security. That is, to tell how, in fact, the topology is formed, routes are built and restored, how external devices are connected and programmed in a standard way — sensors, controllers, actuators. nine0008
That is, to tell how, in fact, the topology is formed, routes are built and restored, how external devices are connected and programmed in a standard way — sensors, controllers, actuators. nine0008
What is 802.1X Network Access Control (NAC)?
What is 802.1X Network Access Control (NAC)?
802.1X Network Access Control (NAC) provides administrators with unified control over access to wired and wireless networks. It is widely used in campus and branch corporate networks and consists of two main elements.
- 802.1X is an IEEE standard for port-based network access control (PNAC) in wired and wireless access points. 802.1X defines authentication elements for any user or device that attempts to access local or wireless networks. nine0134
- Network Access Control (NAC) is a proven networking concept that defines users and devices through network access control. NAC controls access to corporate resources through authorization and policy enforcement.
Problems addressed by 802.
 1X network access control
1X network access control
Wireless access, mobility, bring your own device, social networking and cloud computing have a strong impact on corporate network resources. This enhanced mobility increases the exposure of networks to threats and digital exploitation, as shown in the following figure. Using 802.1X helps to strengthen the inbound security of this type of environment, as well as reduce the total cost of ownership. nine0008
What can I do with 802.1X Network Access Control?
There are many ways to deploy Network Access Control, but the main ones are as follows.
- Pre-Access Control — Block messages that are not authenticated.
- Device and user discovery — Identify users and devices with predefined credentials or machine IDs.
- Authentication and authorization — verification and granting access. nine0134
- Connectivity — Provides the device with security software, site management, and verification capabilities.
- Profiling — endpoint scanning.

- Enforce Policies — Role assignment and permission-based access.
- Control after granting access — forced session termination and cleaning.
802.1X provides Layer 2 network access control by checking the user or device that is trying to access a physical port. nine0008
How does 802.1X network access control work?
The procedure for the 802.1X Network Access Control (NAC) procedure is as follows.
1. Initiating: The authenticator (usually the switch) or the supplicant (client) sends a session initiation request. The supplicant sends an EAP response to the authenticator, which encapsulates the message and forwards it to the authentication server.
2. Authentication: messages are passed between the authentication server and the supplicant through the authenticator in order to verify certain pieces of information.
3. Authorization: If the credentials are valid, the authentication server notifies the authenticator to grant access to the requesting device.